Next named exclusive Trail Blazer in NEW 2024 Radicati DLP Market Quadrant Report
Read the Report

Preventing the loss or theft of protected health information (PHI) and personal identifiable information (PII) is a challenging task.
Healthcare is one of the most targeted industries, with employees being the main source of healthcare data breaches – understandably so as doctors’ and nurses’ jobs aren’t cyber security or technology.
PHI needs to be protected throughout the entire healthcare ecosystem. As healthcare professionals access and share PHI, adherence to policy and process must be followed to prevent data breaches.
While accidental or negligent data loss is most common, intentional data thefts do occur within healthcare. In pharmaceuticals, data theft is common due to high-risk leavers taking confidential data with them when changing jobs to work for a competing company. Security operators struggle with protection against data loss, visibility into unauthorized access and email exfiltration.
HIPAA and GDPR exist in part to protect patients’ PHI. With compliance comes strict regulations and periodic audits, while balancing security controls and protection of patient records.
In addition, as compliance audits have a retrospective approach to looking at previous incidents, many organizations want to shift to a proactive approach to ensure compliance ahead of the audit.
As IT security policies must be continuously updated based on new regulations and directives, hospitals must train staff very frequently.
Healthcare staff are increasingly spending more time in classrooms rather than with patients. This is leading to a huge cost for hospitals, which they are looking to reduce by finding more effective training methods.
Choose Reveal to ensure compliance with laws, regulations and standards, and protect your organization from data loss and data theft in one single platform.
With a combination of data loss, user activity monitoring, and privacy capabilities you can detect and mitigate threats while maintaining the confidentiality of healthcare professionals and patients.
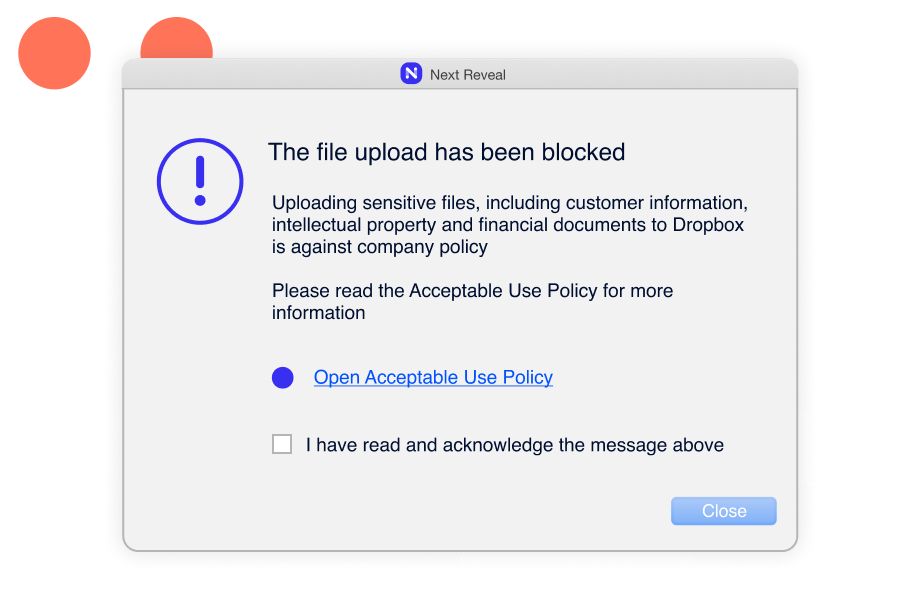
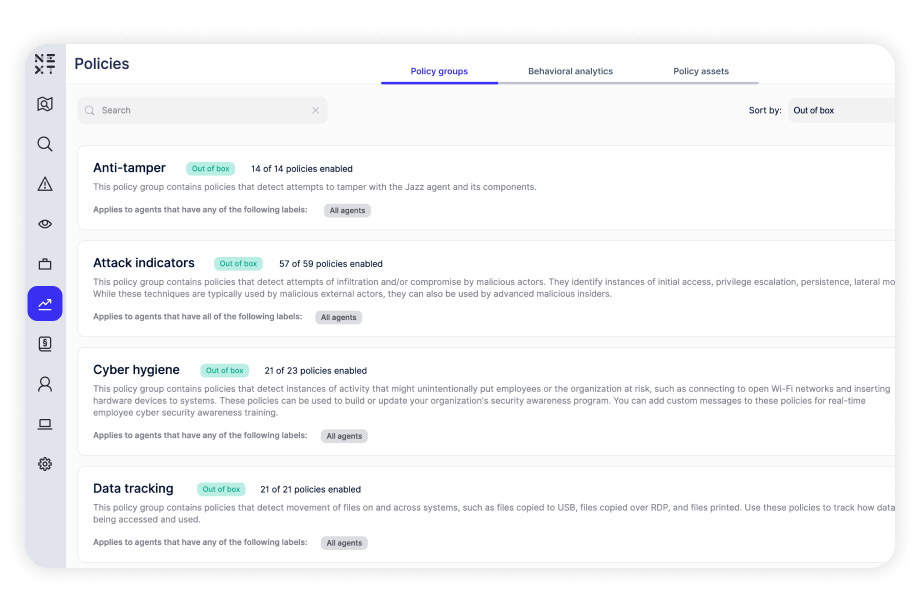
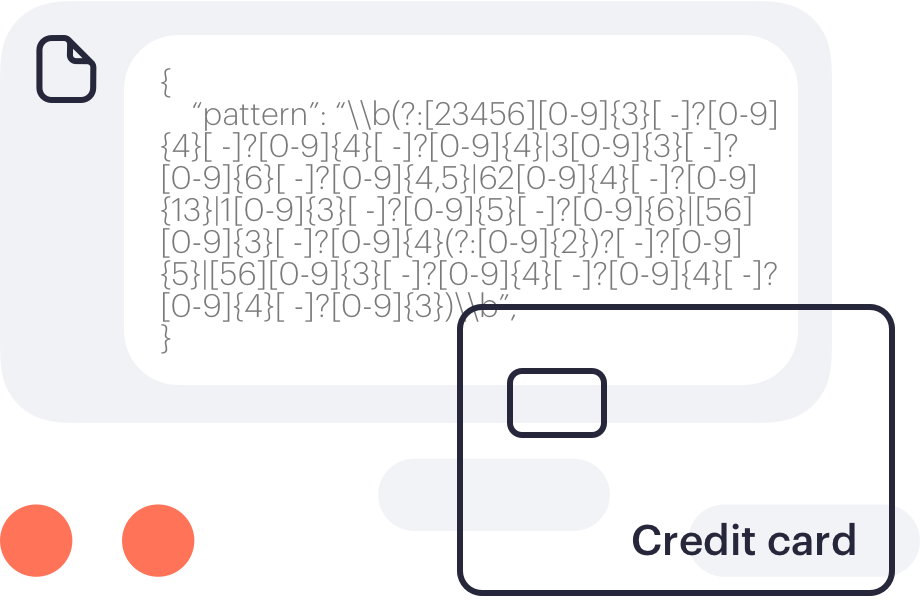
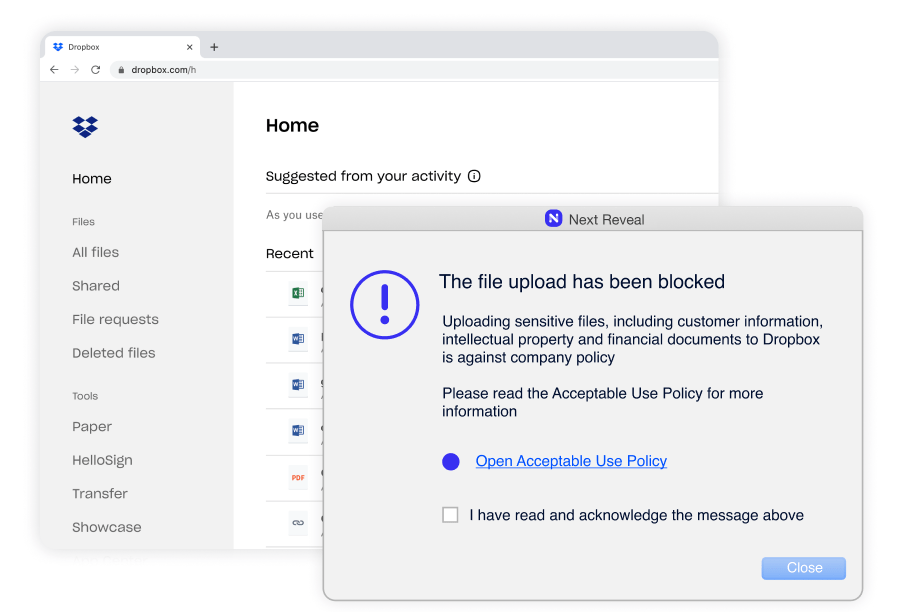
Constant enforcement without exception–whether they are remote or working offline. Enforcing employee adherence to corporate policies such as Acceptable Use Policy (AUP), Information Security Policy (ISP) and more.
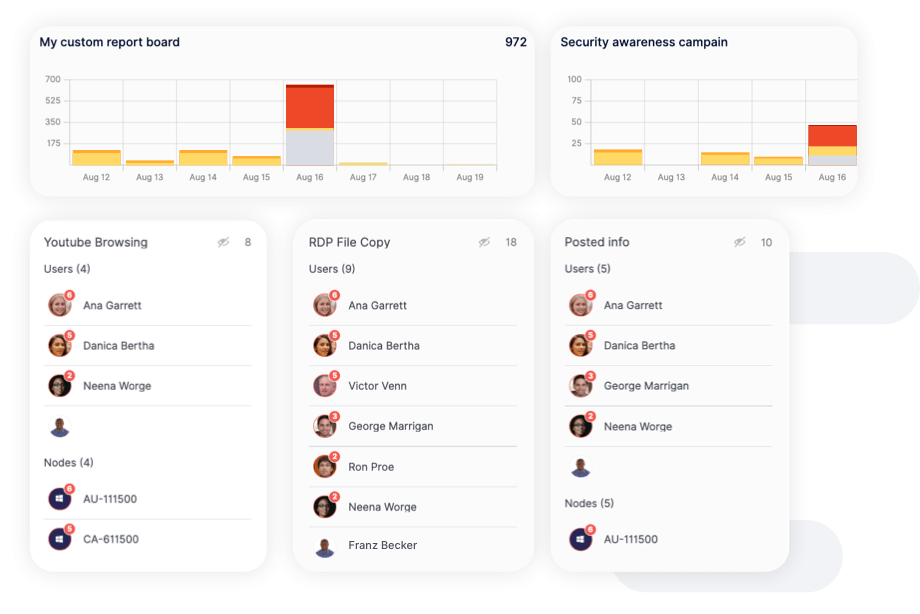
Reports highlight instances of careless, malicious, and accidental behavior over time, allowing you to assess the effectiveness of your security controls and identify areas for improvement. Reports can also be easily exported to share with leadership.