Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Financial services are one of the most targeted industries due to the extensive valuable information they hold - personal information, financial data, trade secrets, and intellectual property - and money. They are subject to both external and internal attacks, whereas over half come from insiders.
Unintentional data loss from insiders is most common. Lack of efficient training on IT security policy makes employees more likely to process, handle and share data incorrectly, fall for phishing attempts, and violate corporate IT security policy.
Financial services are also subject to people stealing data due to high competition between firms and the turnover of employees. Even with vigilant security measures, employees find creative ways to exfiltrate data to disable and circumvent security controls. Legacy DLP solutions fail to identify intent, not providing organizations with the visibility and context needed to do so.
Financial services outsource operations to 3rd-party vendors for cost and efficiency. This opens them up to new risks, as they’re often given privileged access to sensitive data, applications, and systems, which makes them an insider risk. As 3rd parties might not have the same locked-down IT environment in place, the financial services lack visibility to data exfiltrated from their systems.
Financial services include banking, insurance, financial markets, technology trading, asset management, private equity, hedge funds, and more. What they all have in common is that they have confidential data they must protect.
Due to the volume of sensitive information, financial services are also heavily regulated. With today’s retrospective approach to compliance, financial services risk failing their audits. Many organizations are looking to shift to a proactive approach to ensure compliance ahead of the audit.
Customers, regulators, and shareholders scrutinize financial services’ security–one breach or failed audit might be enough for them to leave and have an unrepairable reputation.
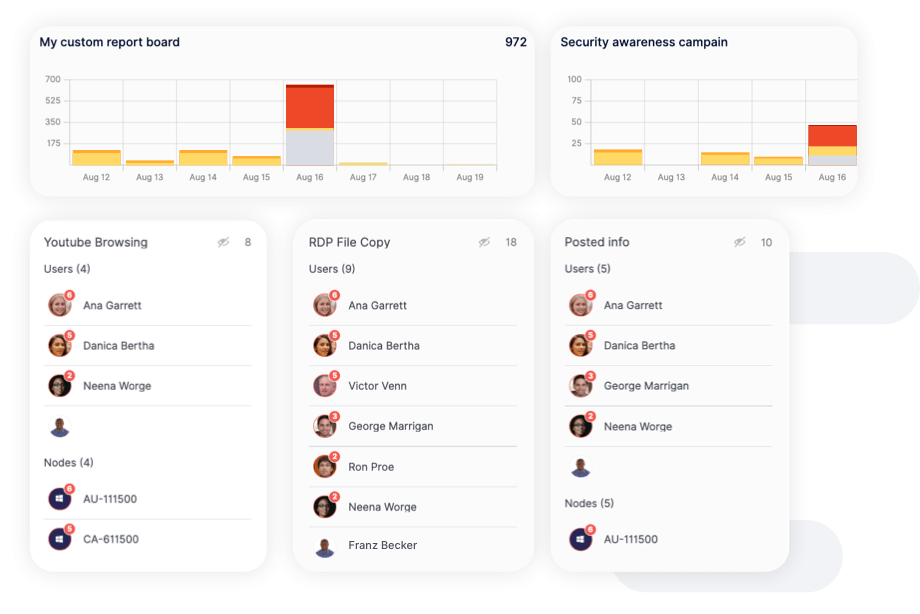
Choose Reveal to get the insight you need to protect valuable data, ensure compliance, identify and manage insider risks, block data exfiltration attempts from malicious insiders, and efficiently educate employees on IT security policies–all in one single platform.


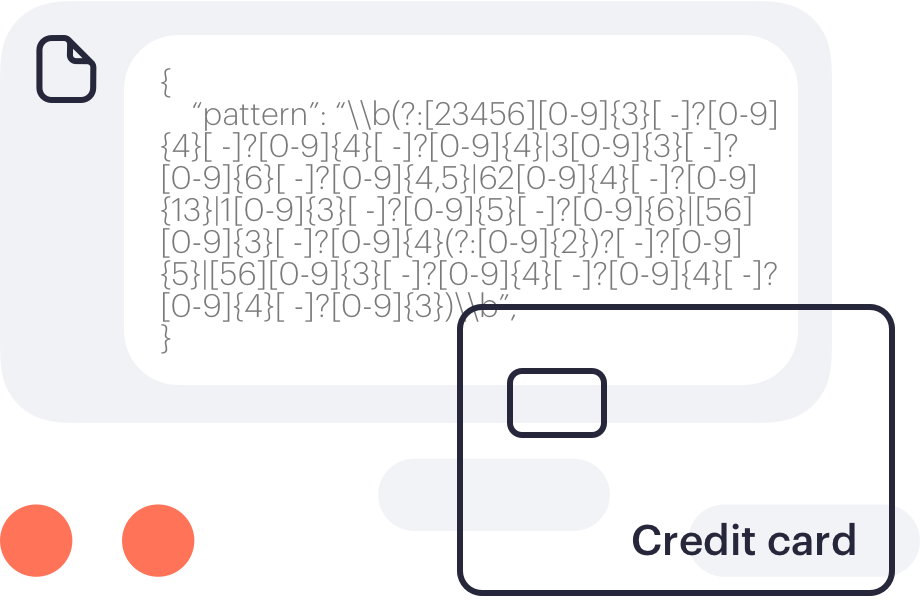
Track file movement on and across systems and browsers with advanced content inspection to protect against data loss. Patterns include credit or debit card numbers, identity card numbers, insurance numbers, social security numbers, and national health service numbers.
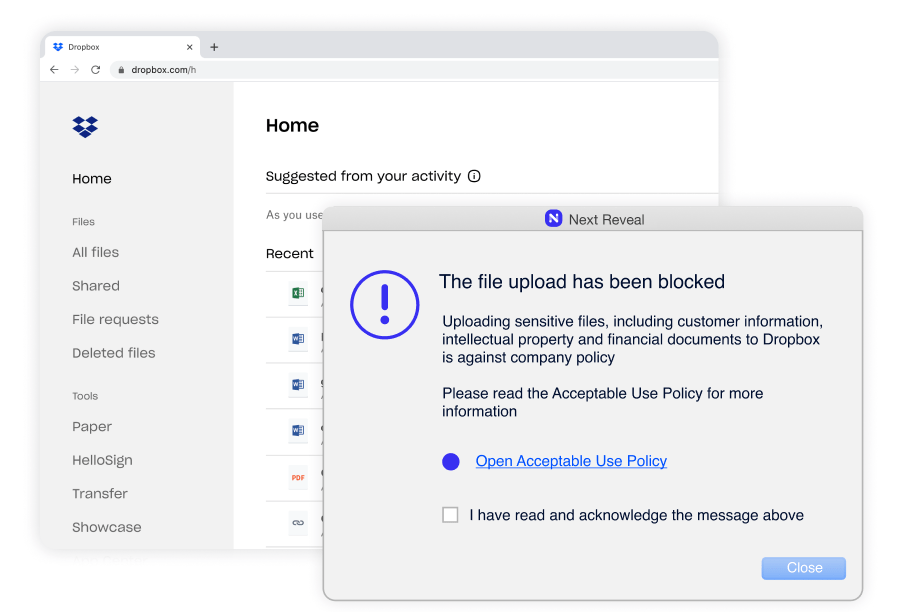
Constant enforcement without exception–whether they are remote or working offline. Enforcing employee adherence to corporate policies such as Acceptable Use Policy (AUP), Information Security Policy (ISP) and more.