Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

For more information about our security practises, documents and certifications. Check out our trust portal at: https://trust.nextdlp.com/
Anyone experiencing a Next DLP product security issue is strongly encouraged to contact the Next DLP PSIRT via security@nextdlp.com. Next DLP welcomes reports from customers, vendors, security researchers, industry organizations, and other stakeholders. Please contact the Next DLP PSIRT via security@nextdlp.com. Support requests will be acknowledged within 48 hours.
General security-related queries
For general security questions, please contact support@nextdlp.com.
How to report a security vulnerability?
If you believe you’ve found a security vulnerability in one of our products or platforms please send it to us by emailing security@nextdlp.com.
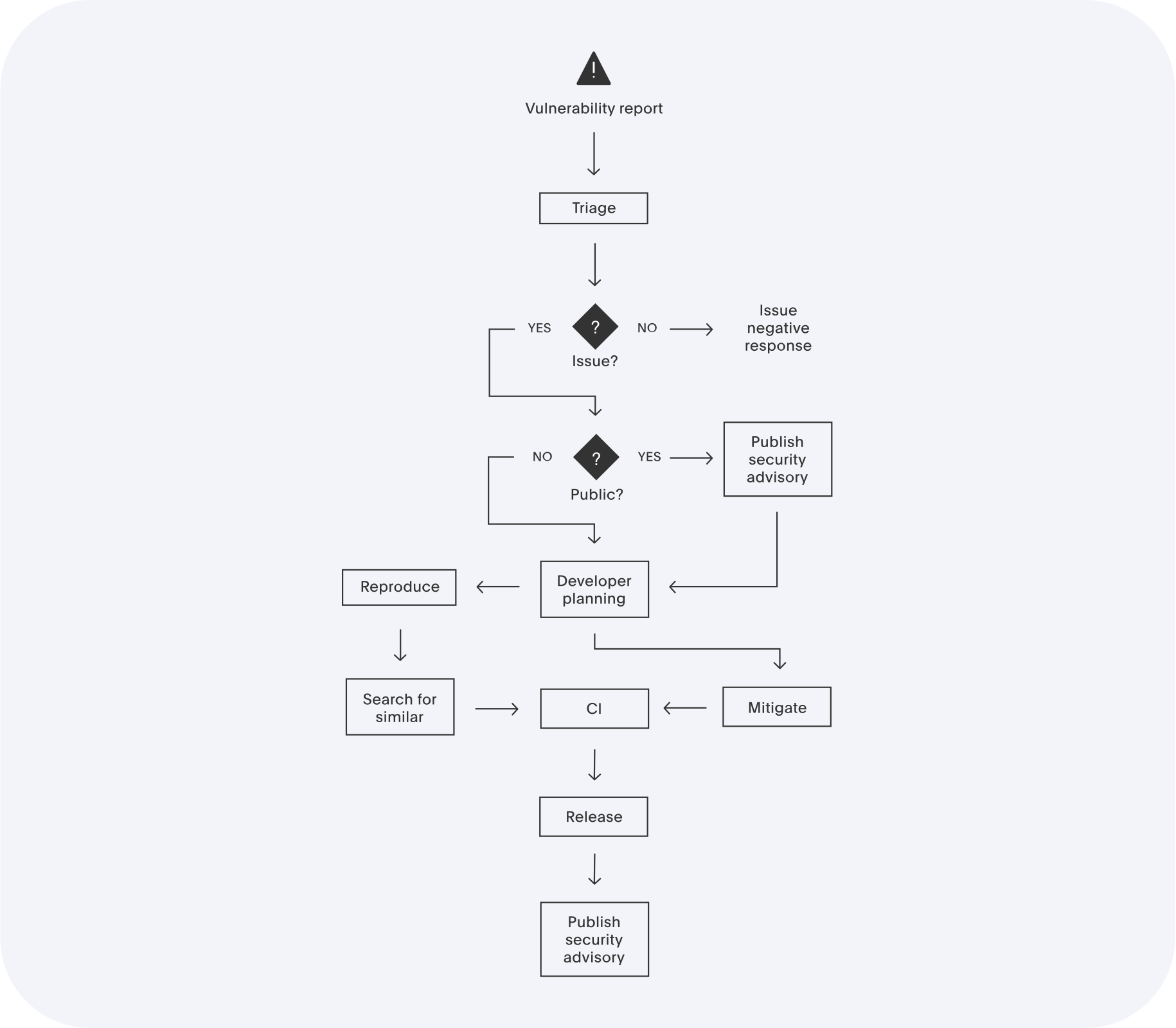
Next DLP takes the security of our customers and its relationship with the security research community seriously. This document outlines what can be expected from Next DLP when a vulnerability is reported and what Next DLP considers to be acceptable for researchers in the process of testing.
We require that all researchers:
If you follow these guidelines when reporting an issue to us, we commit to:
Legally acquired versions of Next DLP software running in a deployment for which the researcher has the rights, or explicit permission, to test are in scope. Security researchers may be provided with trial versions of software for experimentation.
Any services hosted by 3rd party providers and services are excluded from scope. In the interest of the safety of our users, staff, the Internet at large and you as a security researcher, the following test types are excluded from scope:
Things we do not want to receive:
Next DLP is committed to resolving vulnerabilities to meet the needs of its customers and the broader technology community. This document describes Next DLP's policy for receiving reports related to potential security vulnerabilities in its products and services and the company’s standard practice with regards to informing customers of verified vulnerabilities.
Contact the Next DLP Product Security Incident Response Team (PSIRT) by sending an email to security@nextdlp.com in the following situations:
The security@nextdlp.com email address is intended ONLY for the purposes of reporting product or service security vulnerabilities. It is not for technical support information on our products or services. All content other than that specific to security vulnerabilities in our products or services will be dropped. For technical and customer support inquiries, please contact support@nextdlp.com. Next DLP attempts to acknowledge receipt to all submitted reports within 48 hours.
Technical security information about our products and services is distributed through several channels.
All aspects of this process are subject to change without notice, as well as to case-by-case exceptions. No particular level of response is guaranteed for any specific issue or class of issues.
At any point in the process, PSIRT can choose to issue or update a security advisory if the issue becomes public.
Confidentiality
All public communication on the subject of security vulnerabilities is via PSIRT through agreed channels.
Issues which impact (in a way which can be used by an attacker) the Confidentiality, Integrity or Availability (CIA) of installations are considered to be security issues. At this point severity is not considered: if it impacts one of CIA, then it’s a security issue.
Security issues are prioritized by severity using CVSSv3 scoring:
These map to turnaround times as follows:
PSIRT can raise the priority to Critical in response to exploitation in the wild, public disclosure, etc.