Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Any government’s primary security challenge is data loss related to security breaches. Protecting sensitive data from being exfiltrated and falling into the wrong hands is a government’s responsibility to its people.
Some government bodies have in-house document systems to control data. However, these document systems need to be used consistently to be effective. Without enforcing the use of the document systems, the government has no control over what happens to the data that is handled outside the system.
In addition, many government agencies have hundreds or thousands of employees. A lot of these employees may have privileged access to sensitive data and systems. With the high turnover, educating employees becomes a crucial part of improving cyber hygiene.
Faced with limited insight and control, security teams need to understand how data is handled. Choose Reveal–winner of U.S. Cyber Command–to identify and manage risks related to data processing as well as educate employees on IT security and compliance policies.
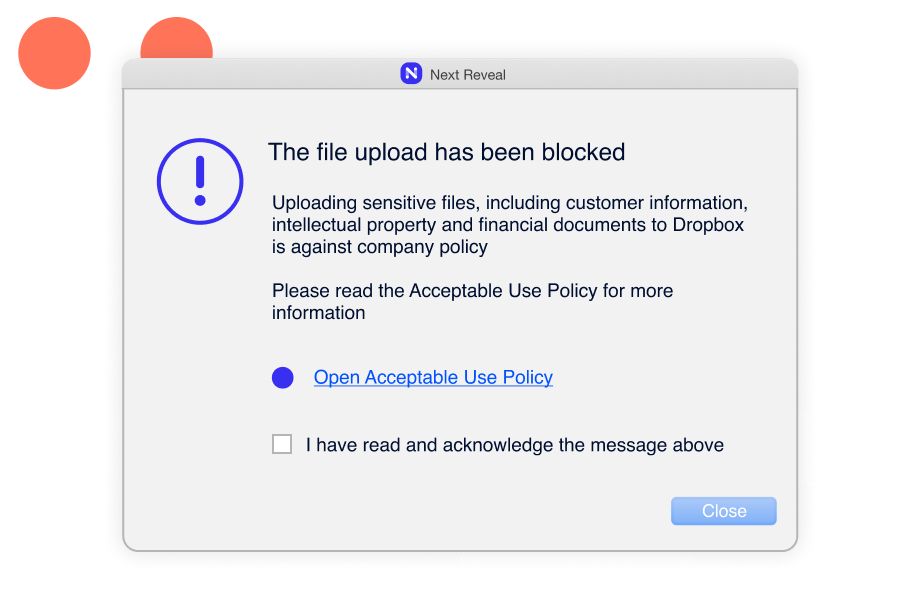

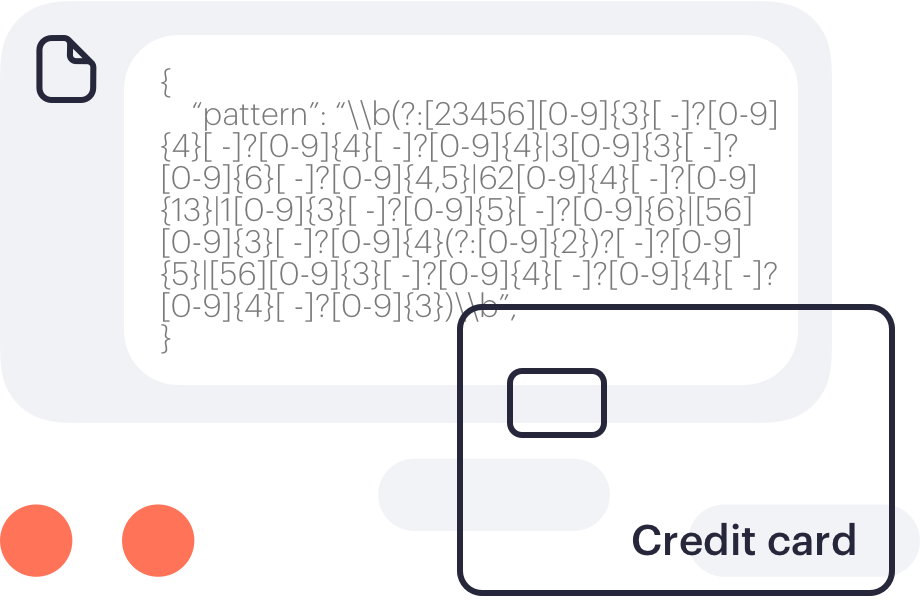
Track file movement on and across systems and browsers with advanced content inspection to protect against data loss. Patterns include credit or debit card numbers, identity card numbers, insurance numbers, social security numbers, and national health service numbers.

Reveal is UAM certified by National Insider Threat Task Force (NITTF), providing individual user profiles, keystroke monitoring, full application content, and screen capture. All data is attributed to a specific user, even on shared machines.