Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Data is at the core of what a business owns. For technology companies, critical intellectual property (IP) including copyrights (source code, designs, arts, databases) and trade secrets (formulas, patterns, processes) need to be protected. They also have other valuable data such as customer lists, employee information, and product roadmaps.
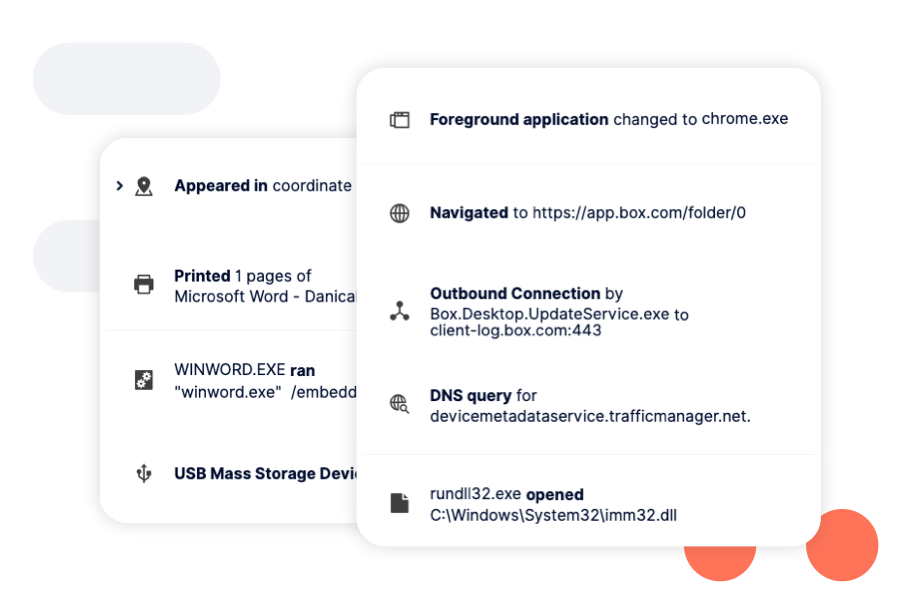
Technology companies need to know who accesses this high-risk data, and when, where and why it is accessed – something they lack visibility into today. Legacy DLP solutions and system-centric solutions such as SIEMs cannot effectively protect the data as they lack the visibility needed.
In addition, visibility into data handling is simply not enough. To efficiently protect the data, companies need to be able to detect, identify, and respond in real-time.
Most technology companies have tech-savvy employees. These employees - with access to sensitive data, servers, and applications - are likely to be sophisticated users who have better knowledge of how to circumvent security measures and therefore pose a major risk.
Choose Reveal to identify and manage risks associated with employees accessing critical IP, prevent data exfiltration attempts and educate employees on how to handle data correctly.

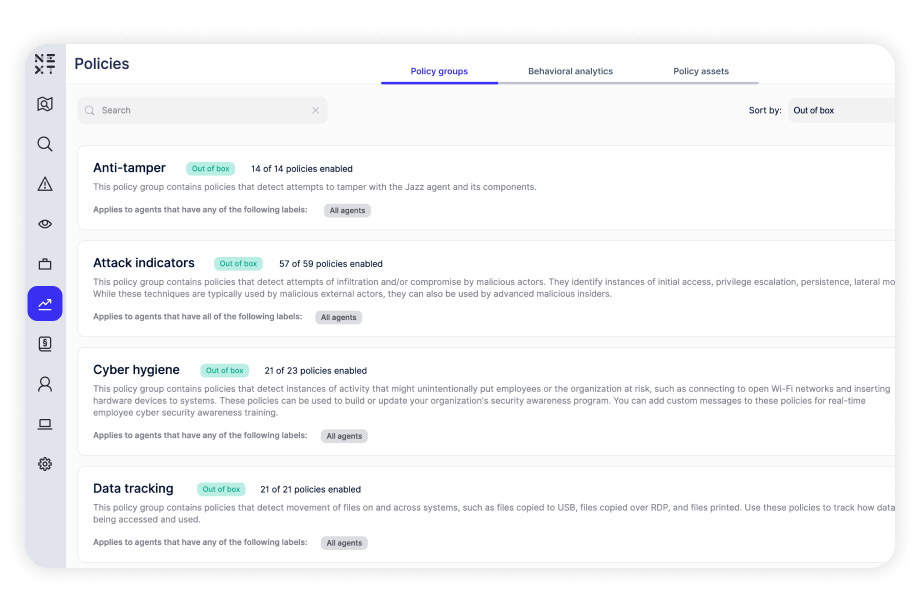
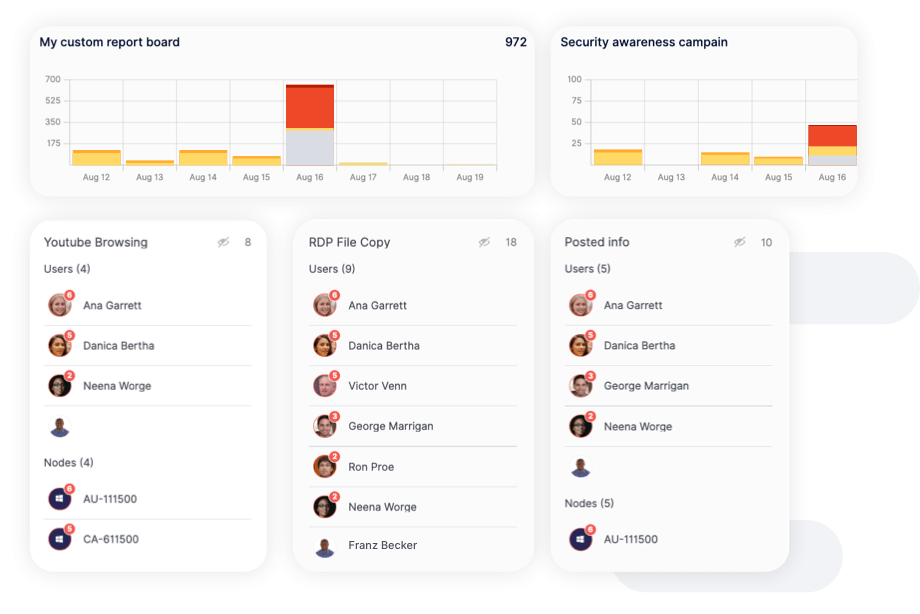
Built-in policies for data tracking, cyber hygiene, and malicious activity that can detect and defend against various risks. Policies run against computers and users, providing insight into how users access files, applications, and systems, which determine specific areas of risk.
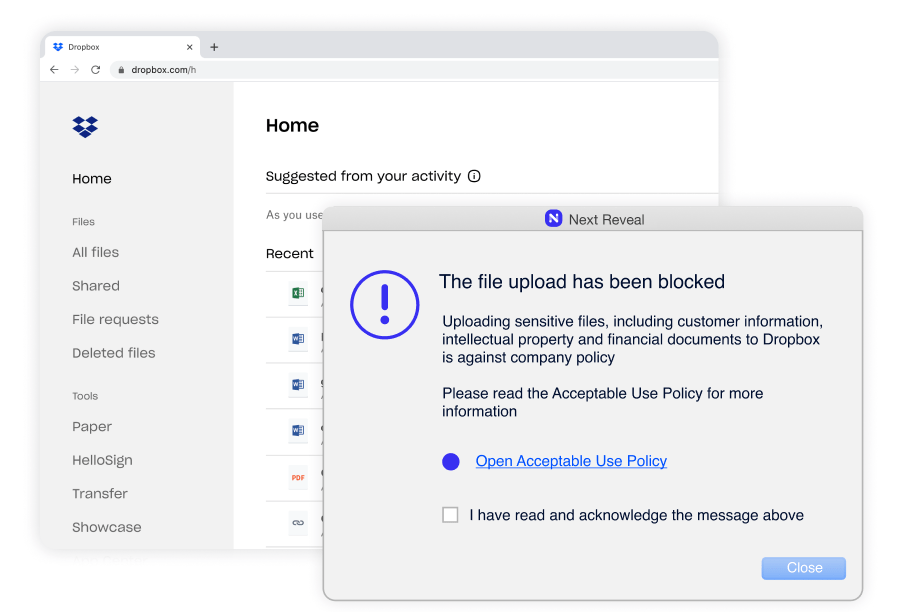
Constant enforcement without exception–whether they are remote or working offline. Enforcing employee adherence to corporate policies such as Acceptable Use Policy (AUP), Information Security Policy (ISP) and more.