Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

According to a study by Cisco, 80 percent of end users install software that is not cleared by IT and the average organization uses 1,220 cloud services. Managing data movement across these environments using legacy DLP and granular rules is not practical. The traditional security umbrella of separate products and multiple agents such as DLP, UBA, CASB and ITM, no longer works.

Reveal provides comprehensive visibility into user interactions with data within the cloud and maintains protection as data moves out of the cloud. This ensures continuous protection of sensitive information, regardless of its location or access method.
Secure Data Flow enhances cloud data security by tracking data's origin, movements, and modifications. It ensures sensitive information in SaaS applications like Salesforce, Workday, SAP, and GitHub is always protected. Secure Data Flow offers detailed insights into data manipulation and egress, preventing data theft and unauthorized access.
By concentrating on data origin and flow, Secure Data Flow delivers a robust, false-positive-free solution that simplifies cloud data protection for organizations.
.png?width=330&height=206)
Due to the lack of visibility and control, shadow SaaS heightens the chance of data leakage and compliance violations as employees may inadvertently leak confidential data through unapproved cloud applications.
Reveal SaaS App Security provides full visibility into the expanse of SaaS applications utilized across an organization and also fortifies defenses against potential data breaches stemming from business data exposure via unauthorized app usage.
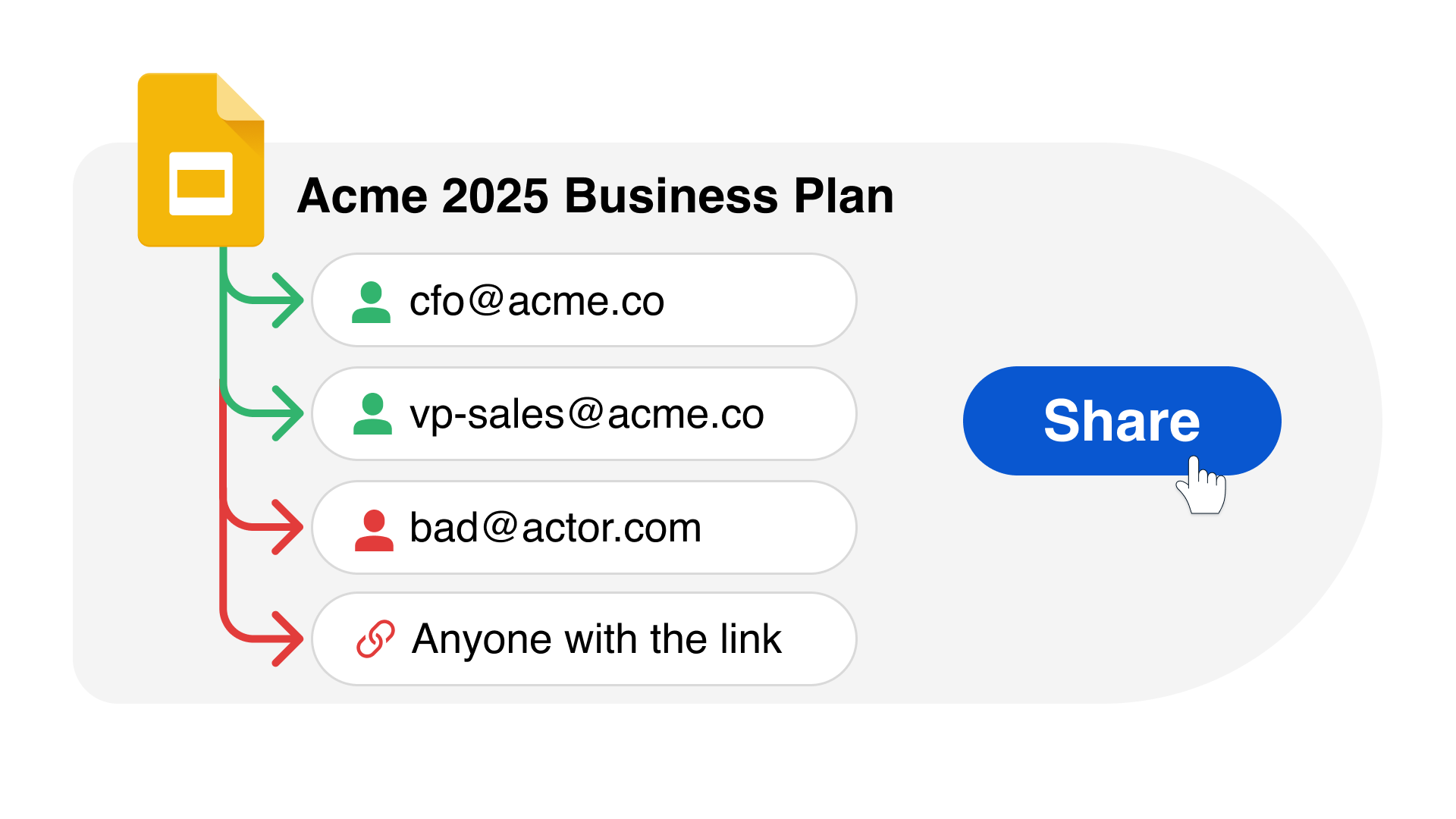
Reveal Beyond overcomes legacy DLP challenges by providing a unified platform for managing data security and extending insider threat visibility and data protection to Microsoft O365, Google Workspace and personal devices.
Reveal Beyond doesn’t require endpoint agents or on-prem technology and effectively addresses DLP and insider risk use cases commonly seen with the use of cloud drives and unmanaged personal devices. Investigation and remediation processes are streamlined to reduce exposure to security risks and compliance challenges.

Reveal identifies and classifies structured and unstructured data instantly, every time a user accesses a file. Machine learning on the endpoint allows Reveal to make faster decisions to train employees and stop data loss without affecting user productivity.
Protect sensitive data
Real-time content inspection identifies PHI, PII, PCI, and other sensitive information across SaaS applications to prevent copy/paste and screenshot data exfiltration.

The Reveal Platform serves as a powerful complement to a Cloud Access Security Broker (CASB) by offering a unique set of capabilities focused on data loss prevention and the secure management of sensitive information within an organization.
While CASBs primarily provide visibility, compliance, data security, and threat protection for cloud environments, the Reveal Platform enhances this ecosystem by offering advanced data protection features, such as sensitive data discovery, real-time monitoring, and comprehensive data leakage prevention. It helps in identifying and mitigating risks associated with data exposure and loss across both cloud and on-premises environments.
This synergy ensures that organizations can maintain a robust security posture, safeguard critical data against evolving threats, and comply with regulatory requirements, thereby securing their digital transformation journey comprehensively.


