Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Manufacturing operators handle classified data and confidential information across corporate IT and operational systems.
Manufacturing organizations are usually hesitant to adopt new security technologies, fearing they will impact critical systems. Any effect on critical systems could result in slowed production and lost revenue.
For those manufacturing companies with lean IT and security teams, some lack the tools needed to get visibility across platforms and effectively protect their organization.
The tools in place are siloed, and hard to identify and investigate incidents across platforms.
Insider risks exist in all organizations. Within manufacturing, insiders are likely to target patents (machines, devices, composite materials, designs) and trade secrets (formulas, techniques, processes).
With the current systems in place, manufacturing companies lack the capability to identify, detect, and respond to suspicious user activity and data movements.
Choose Reveal to detect and block data exfiltration attempts at a cost-effective price point with no hidden costs and a lightweight agent using minimal CPU.
Reveal is easy to deploy and use–even for tier 1 Analysts–giving visibility into user and data activity, systems and processes.
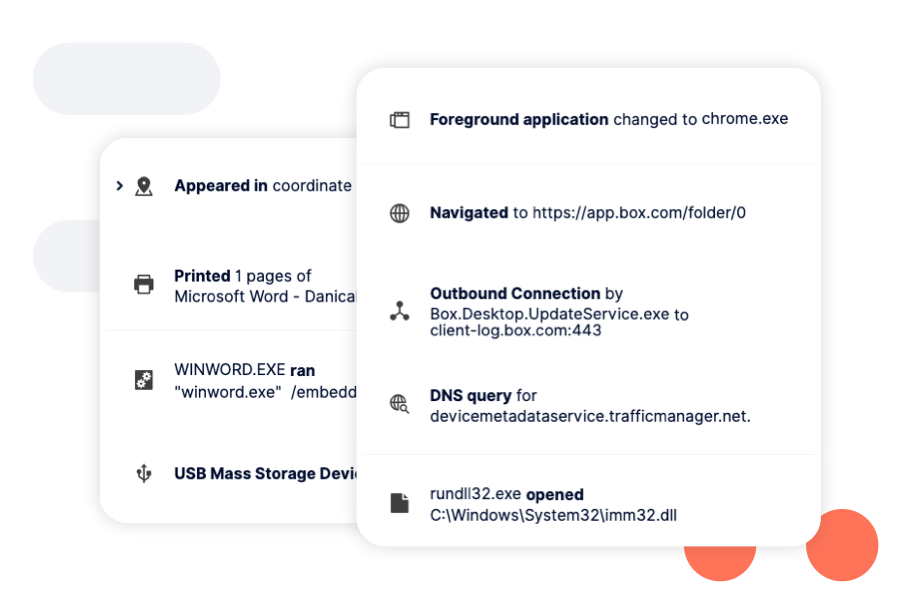

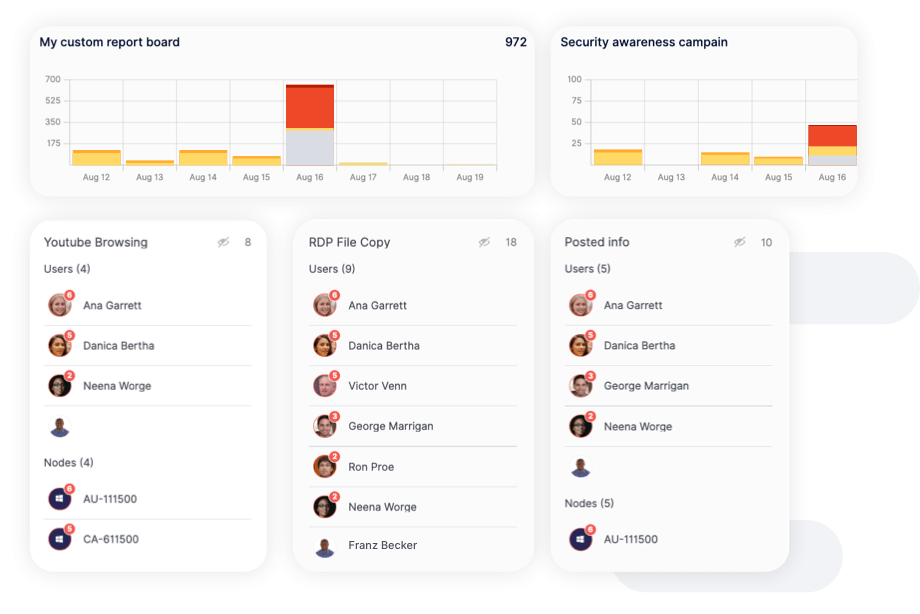
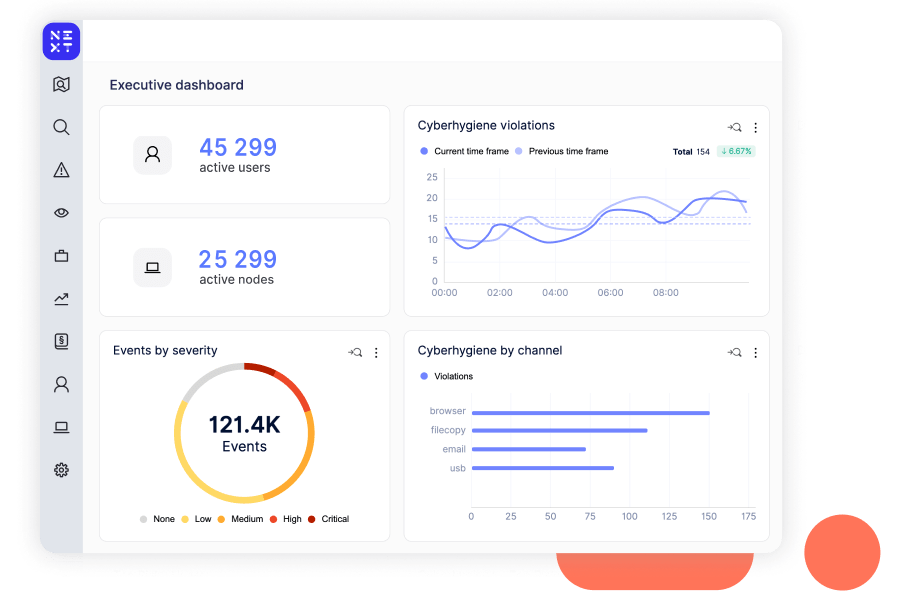
Reports highlight instances of careless, malicious, and accidental behavior over time, allowing you to assess the effectiveness of your security controls and identify areas for improvement. Reports can also be easily exported to share with leadership.
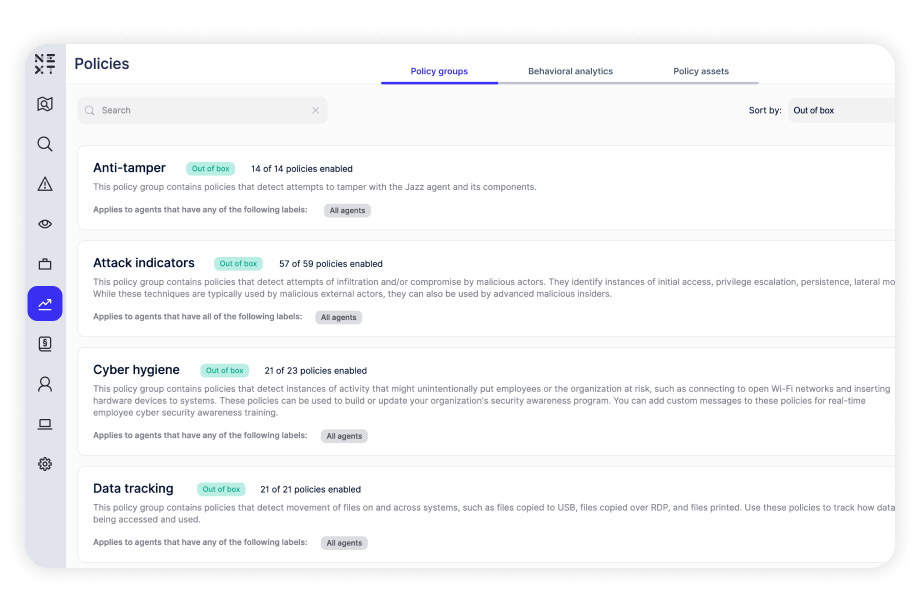
Built-in policies for data tracking, cyber hygiene, and malicious activity that can detect and defend against various risks. Policies run against computers and users, providing insight into how users access files, applications, and systems, which determine specific areas of risk.