Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release


Organizations’ IT team want to reduce the time and costs of periodic employee security training. Teams cannot effectively identify which employees need training the most, so they send all staff to all training sessions, taking them away from their regular work. The IT security policy is continuously updated based on new regulations and directives, and organizations must train staff on every update. However, organizations are struggling to engage staff.
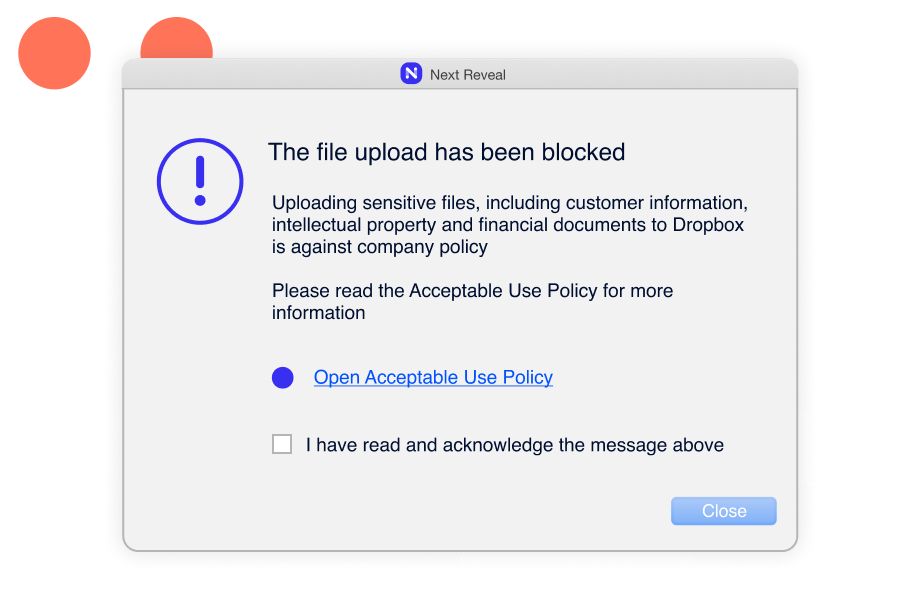
Most employees are not familiar with the intricacies of IT policies they sign when joining a company. Reveal brings those policies to life and helps educate the employees as well as enforce the policies.
Individual user profiles shed light on how data is accessed and used, with optional anonymization for privacy. With user activity monitoring, you can protect your systems and data from those who already have privileged access and knowledge of sensitive data and systems.
With incident-based training, you can train your employees to make the right decisions on detection of unacceptable behavior, reinforce corporate security policies, and promote good cyber hygiene. Achieve a lasting impactful effect with adaptive IT security policy enforcement.
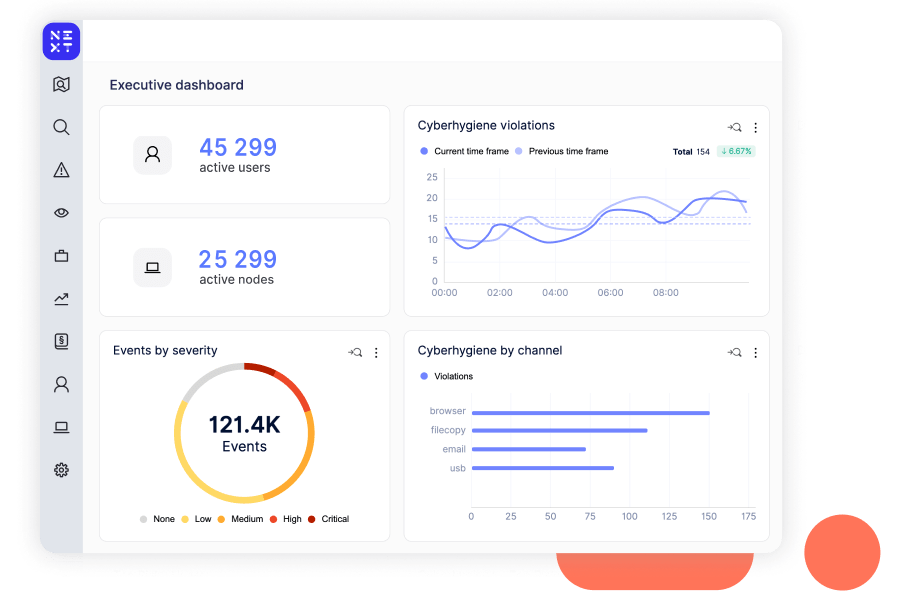
Pre-built rules detect poor cyber hygiene practices, such as employees uploading confidential files to unexpected locations, connecting to unsecured Wi-Fi networks, inserting malicious hardware devices, or using unsanctioned applications for cloud or USB storage.
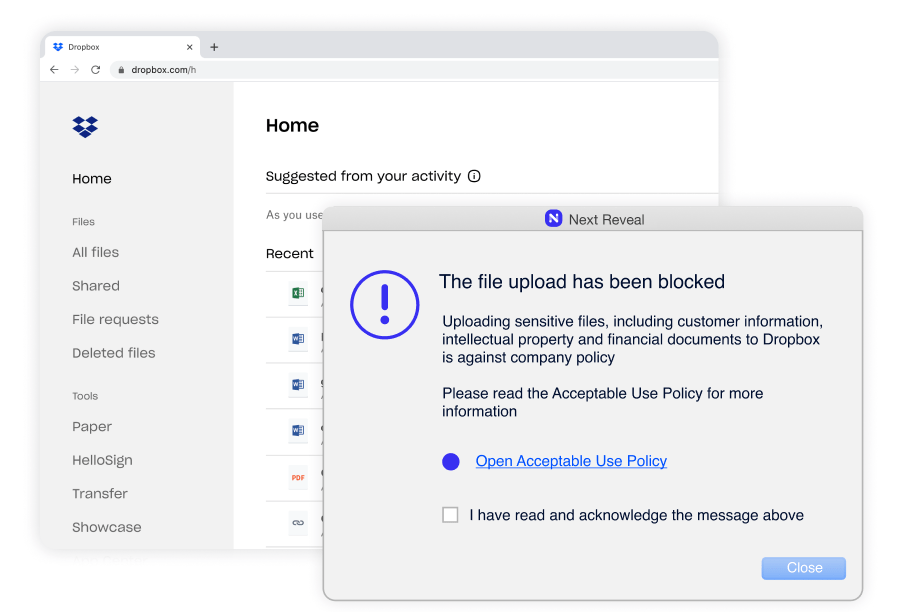
Constant enforcement without exception–whether they are remote or working offline. Enforcing employee adherence to corporate policies such as Acceptable Use Policy (AUP), Information Security Policy (ISP) and more.
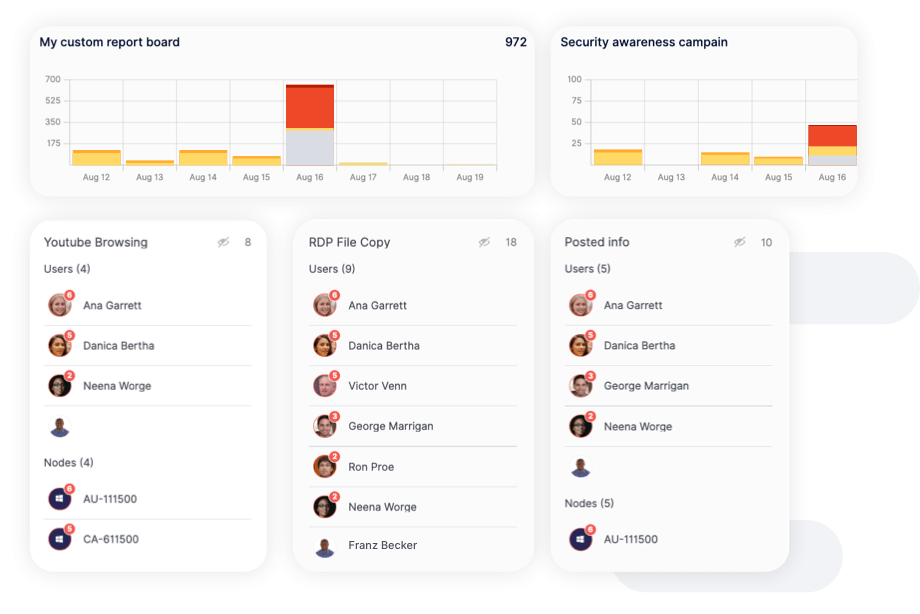
Reports highlight instances of careless, malicious, and accidental behavior over time, allowing you to assess the effectiveness of your security controls and identify areas for improvement. Reports can also be easily exported to share with leadership.

Reveal is simple to use, even for tier 1 analysts. Increase operational efficiency with rich contextual knowledge presented in a comprehensible view. Use machine learning and smart sensors to detect risks before they become incidents.
