Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
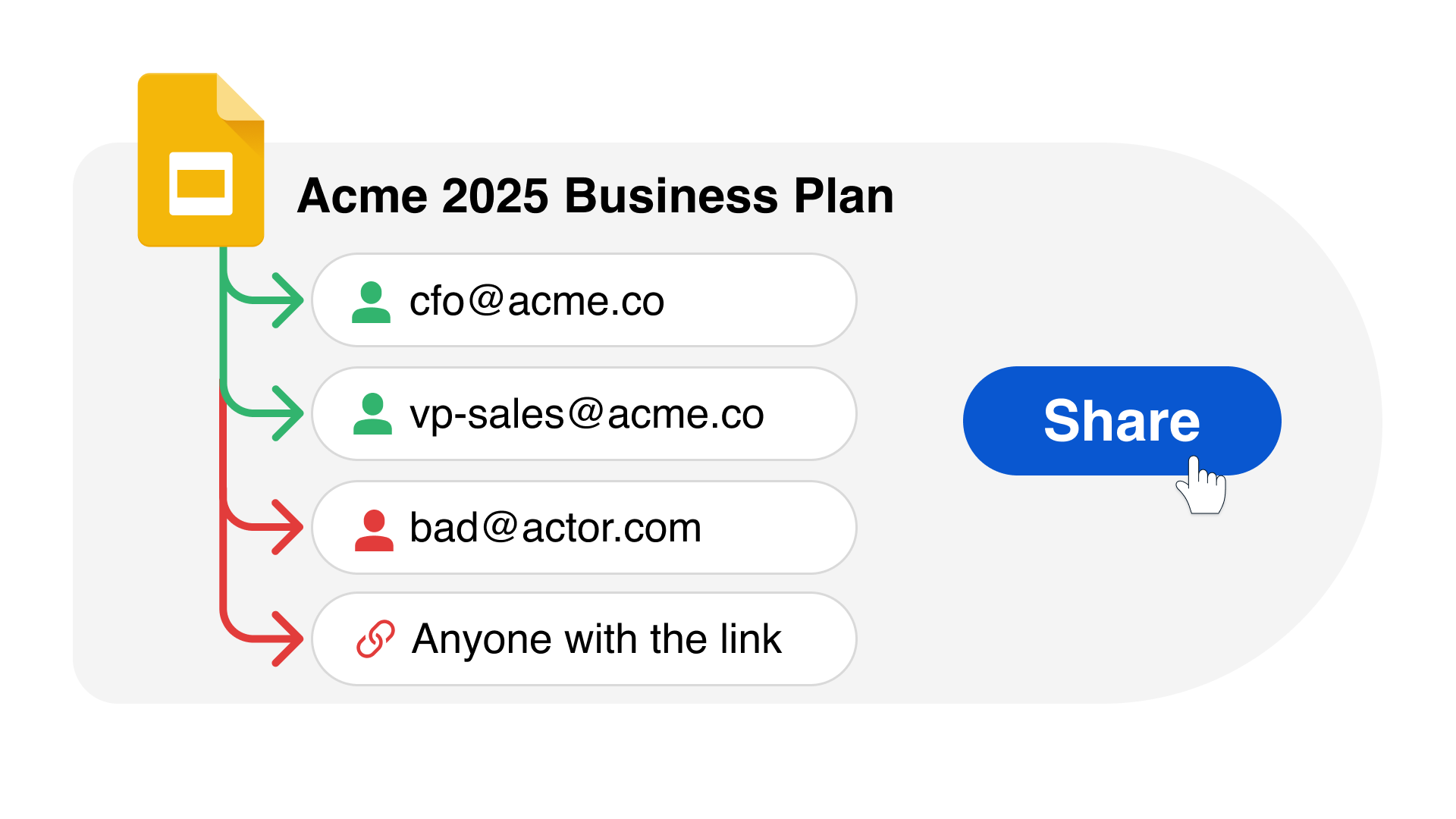
Reveal monitors sanctioned cloud app activities, including on personal, unmanaged devices. It tracks activity from initial reconnaissance - identifying which folders users access and tagging origin details when files are copied - to detecting potential data exfiltration to mobile devices.
At any stage, policies can enforce access restrictions, or alternatively, Reveal can engage the employee with targeted training, turning them into an integral part of their organizations's security solution.
.png?width=330&height=206)
Reveal Beyond overcomes legacy DLP challenges by providing a unified platform for managing data security and extending insider threat visibility and data protection to Microsoft O365, Google Workspace and personal devices.
Reveal Beyond doesn’t require endpoint agents or on-prem technology and effectively addresses DLP and insider risk use cases commonly seen with the use of cloud drives and unmanaged personal devices. Investigation and remediation processes are streamlined to reduce exposure to security risks and compliance challenges.

Due to the lack of visibility and control, shadow SaaS heightens the chance of data leakage and compliance violations as employees may inadvertently leak confidential data through unapproved cloud applications.
Reveal SaaS App Security provides full visibility into the expanse of SaaS applications utilized across an organization and also fortifies defenses against potential data breaches stemming from business data exposure via unauthorized app usage.

