Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

|
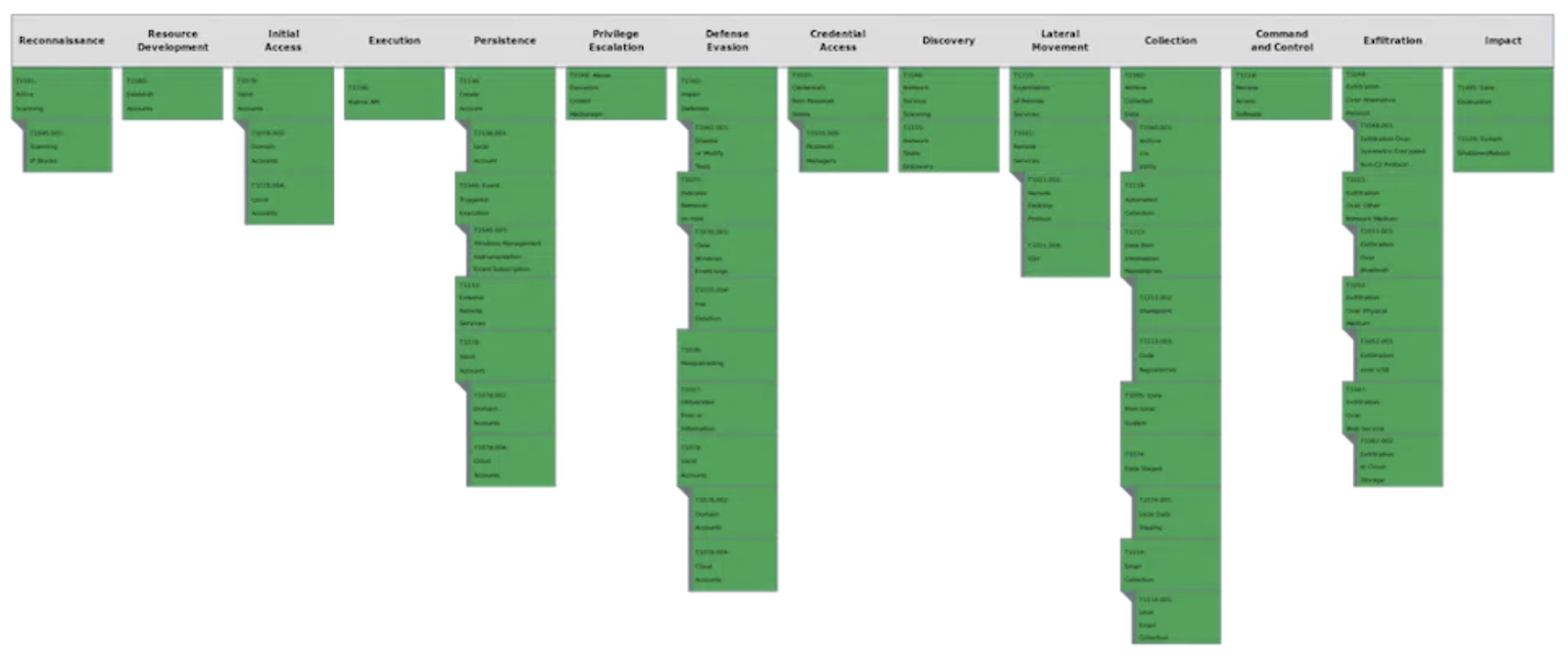
The Center for Threat-Informed Defense, under the administration of MITRE Engenuity, is a non-profit research and development entity funded by private sources. At its core, the Center is dedicated to propelling the frontiers of theoretical and practical cybersecurity knowledge in global threat-informed defense. It brings together diverse participant organizations worldwide, each boasting highly skilled security teams. Leveraging MITRE ATT&CK as a cornerstone, the Center extends the boundaries of threat-informed defense, a critical framework that security teams and vendors utilize to bolster their enterprise security operations.
Mitre’s Center for Threat-Informed Defense, which Next DLP (Next) joined in 2023, took a proactive step by establishing the Insider Threat Knowledge Base in response to the pressing concerns posed by insider threats and the imperative for practical data. This resource serves as a comprehensive repository, meticulously documenting insiders' tactics, techniques, and procedures (TTPs) to carry out detrimental activities. Disseminating this critical information to the public empowers insider threat programs with evidence-based research to enhance their detection and mitigation strategies. The Knowledge Base serves as a vital hub for aggregating and disseminating TTPs utilized by insider threats across a broad spectrum of organizations and sectors.
Insider threats have become a dominant concern for organizations in the ever-evolving realm of cybersecurity. These threats, stemming from within trusted circles of employees and associates, often involve sophisticated tactics that are challenging to detect and prevent. To address this issue effectively, Next's Reveal Platform offers a robust solution that aligns with the MITRE Insider Threat Knowledge Base, providing organizations with a powerful defense mechanism against insider threats.
Insider threats represent a multifaceted challenge in the world of cybersecurity. They encompass a broad spectrum of malevolent or inadvertent activities carried out by individuals with legitimate access to an organization's systems, data, and resources.
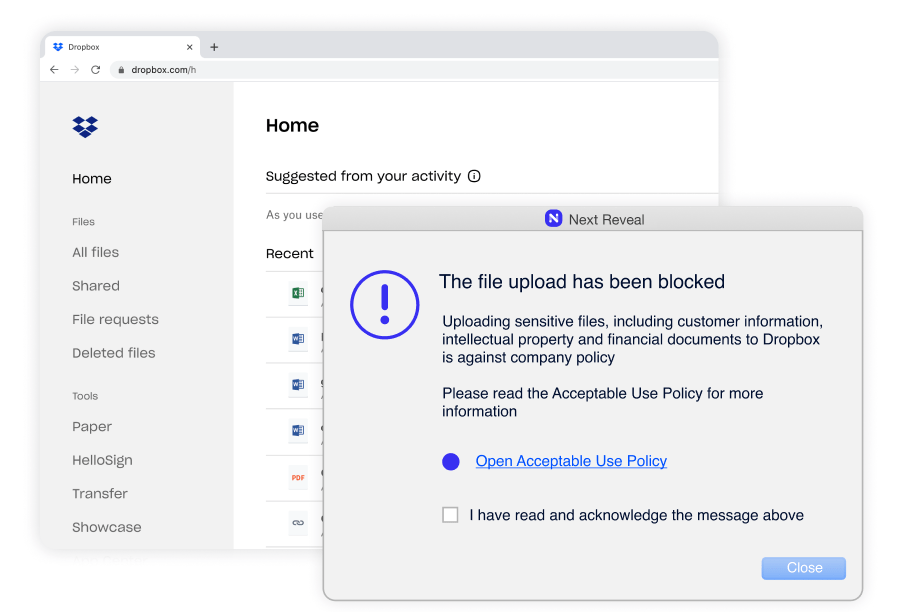
Executives hate surprises, particularly unforeseen data events. The Reveal Platform from Next learns what normal data movement and use look like in your environment, distinguishing between a user mistake and malicious intent. It’s a purpose-built solution to help organizations proactively identify and mitigate insider threats. It protects critical assets on and off the network, providing the visibility and control to prevent data loss in business-critical applications.

|
Next's Reveal platform aligns with the MITRE Insider Threat Knowledge Base, offering organizations a comprehensive security solution that provides an integrated defense against insider threats. Here's a breakdown of how Reveal maps to the techniques of the MITRE Insider Threat Knowledge Base:
MITRE's Knowledge Base emphasizes the techniques employed by insider threats to exfiltrate data without authorization. Specifically, exfiltration over Bluetooth, Network, USB, Web Service to Cloud Storage and encrypted network protocol. Reveal's robust DLP capabilities monitor the access and movement of data across the most common exfiltration vectors and identify unauthorized use, ensuring that sensitive information doesn’t leak from the organization and fall into the wrong hands.
|
Insider threats often move laterally within an organization to access sensitive data. Based on the center’s participant-validated evidence, lateral movement of data ATT&CK techniques used by insiders include exploiting Remote Services, including Remote Desktop Protocol (RDP) and SSH. Reveal goes beyond mere access control by continuously monitoring and analyzing user behavior. It can identify unusual patterns, such as privilege escalation, unauthorized access, and lateral movement, offering invaluable insights to counteract potential threats.
|
MITRE recognizes the common occurrence of credential misuse from password stores and managers in insider threat scenarios. Reveal closely monitors user access and swiftly identifies anomalies in login patterns, making it easier for organizations to identify and rectify potential security breaches. As part of an incident-based training program, Reveal can be used to train employees to double-check links and prompts that may be embedded in Phishing emails before entering a username and password combination.
|
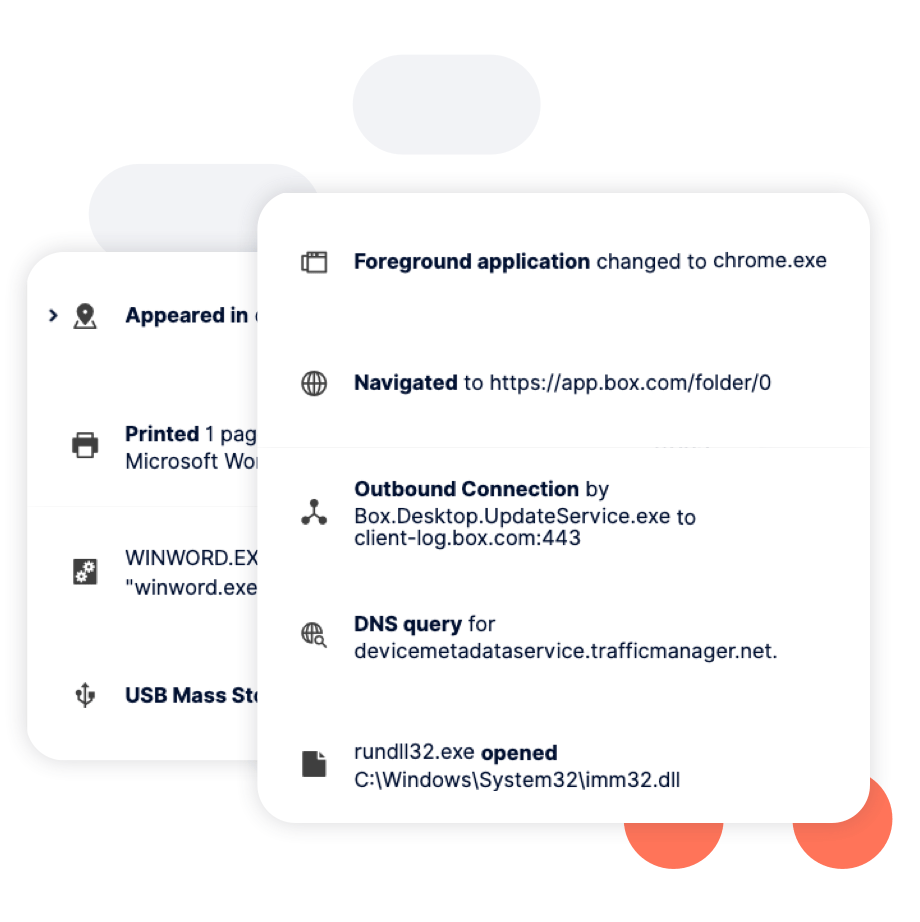
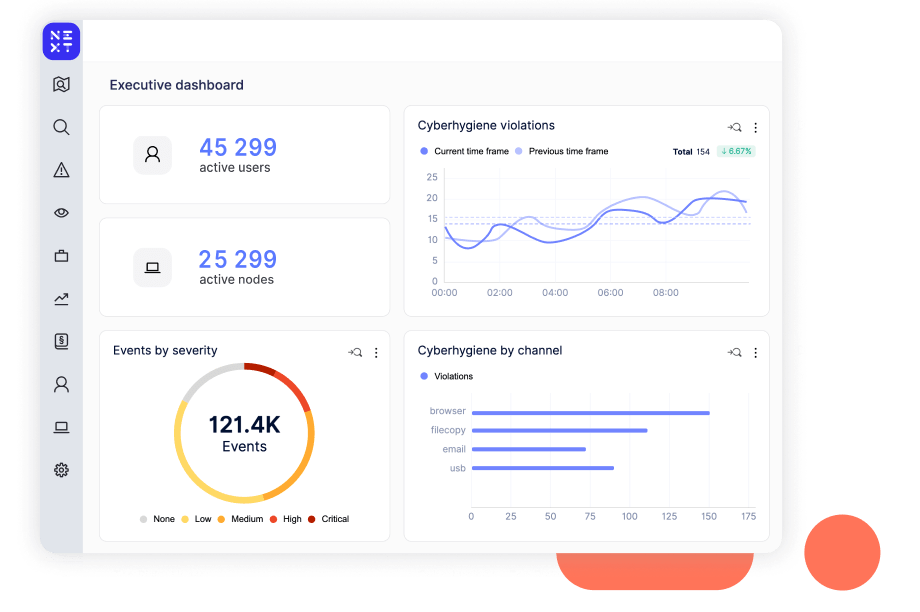
MITRE's insider threat knowledge base underscores the importance of identifying anomalies in user behavior. The knowledge base calls out that malicious insiders use reconnaissance, access and discovery techniques, such as scanning and service and account access, to carry out detrimental activities. Reveal leverages sophisticated machine learning algorithms to detect unusual activities and deviations from established norms. This enables organizations to respond promptly to insider threats, reducing the risk of data breaches and intellectual property theft.
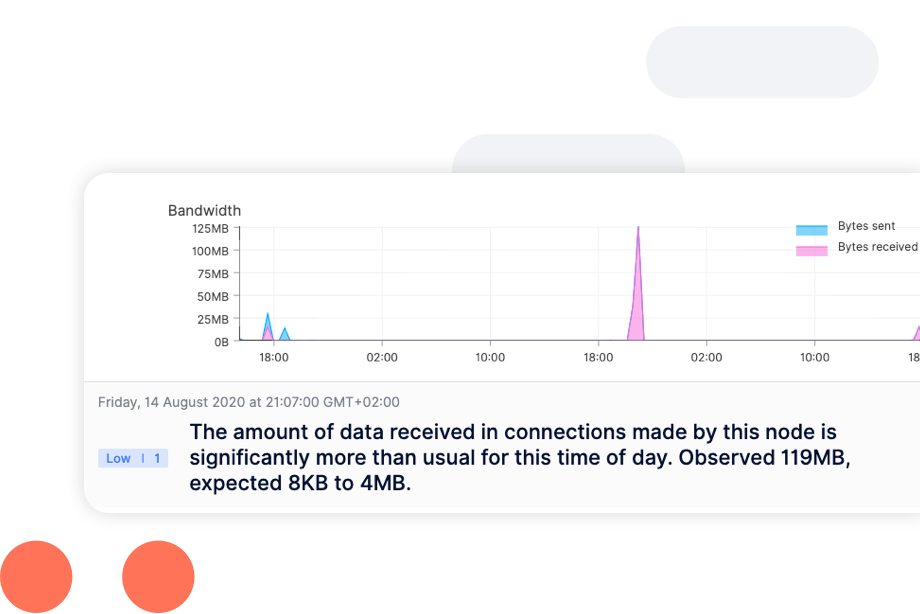
|
Reveal brings together and correlates multiple indicators of compromise, from Defense Evasion to Impact techniques. Techniques that Reveal can alert on include defense evasion, such as disabling or modifying tools, renaming files, deleting or destructing files, and clearing event logs. These techniques equip organizations with actionable threat intelligence, aligning with MITRE's recommendations to collect and analyze relevant indicators. This comprehensive approach enhances threat detection and response, ensuring organizations can swiftly adapt to emerging threats, such as limiting a suspicious endpoint by isolating it from the network or locking it so the user cannot use it.
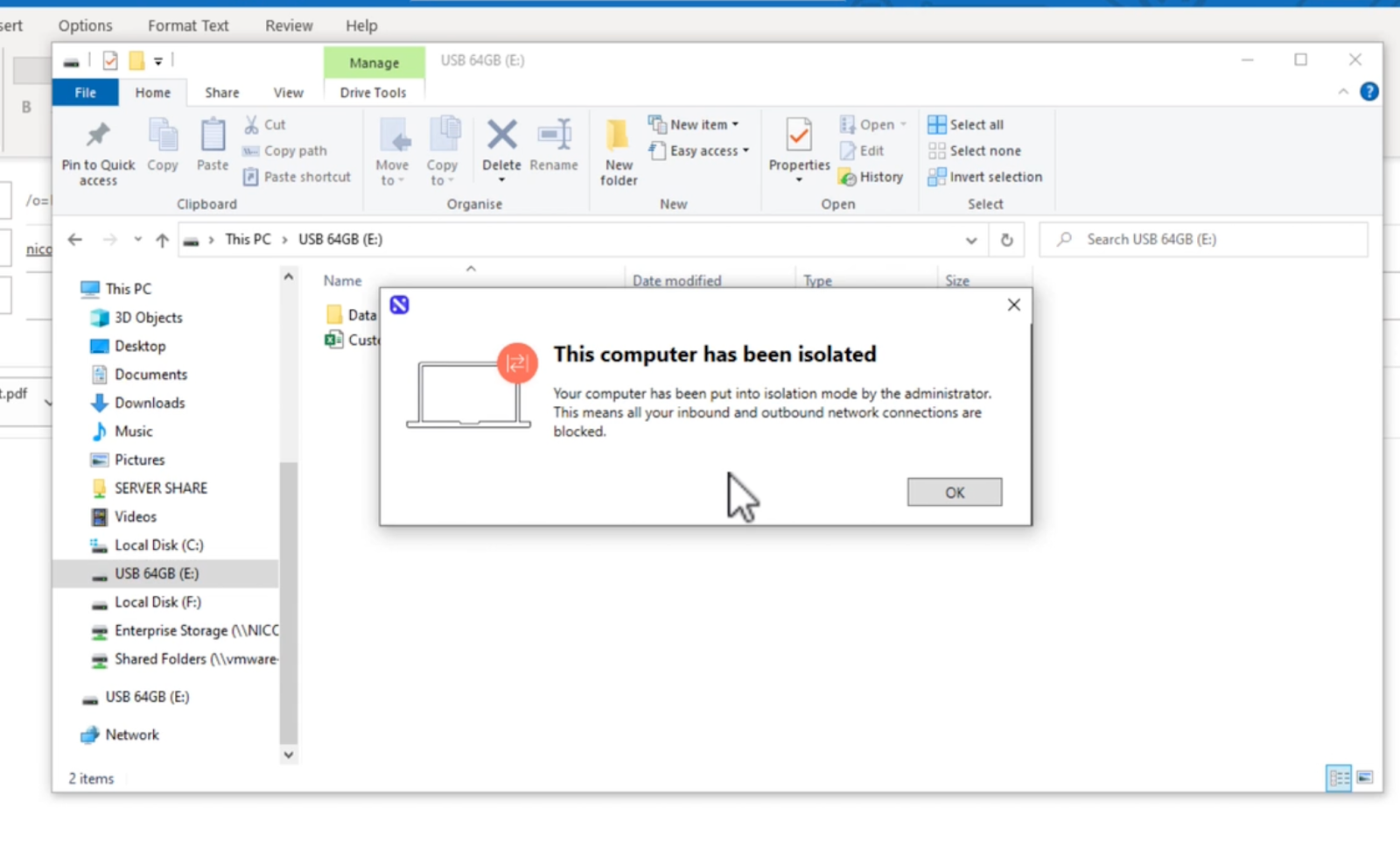
|
Insider threats are a significant risk to an organization's sensitive data and intellectual property. In a landscape where security is paramount, having the right tools and strategies in place is non-negotiable. Next's Reveal platform offers an exceptional solution that closely aligns with the MITRE Insider Threat Knowledge Base, providing organizations with a robust defense against insider threats.
By leveraging the Reveal platform, organizations can proactively safeguard their digital assets, quickly detect insider threats, and respond effectively. The alignment with the MITRE Insider Threat Knowledge Base empowers businesses to establish a comprehensive and data-centric approach to insider threat mitigation, ensuring the safety and security of their sensitive information and intellectual property. With Reveal, organizations are better equipped to navigate the complex landscape of insider threats and protect their most valuable assets. Where before, organizations lacked true insight into the risks posed by insiders and their devices, with Reveal, now they know.
https://mitre-engenuity.org/wp-content/uploads/2022/12/Insider_Threat_Knowledge_Base.png.webp

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
