Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Key Points:
Cloud Security Posture Management (CSPM) and Data Security Posture Management (DSPM) are two critical aspects of an organization's security infrastructure that address different, yet interconnected, facets of cybersecurity. This blog post will delve into the key differences between CSPM and DSPM solutions, their importance, and how they complement each other to ensure a comprehensive security strategy.
Cloud Security Posture Management (CSPM) is a cybersecurity approach that focuses on identifying and rectifying misconfigurations and compliance violations within cloud environments. As organizations migrate to cloud services, the complexity and dynamism of these environments have made traditional security measures inadequate. CSPM solutions automate the discovery and remediation of risks associated with cloud infrastructure, ensuring continuous compliance and security posture management. CSPM solutions primarily focus on the following areas:
Data Security Posture Management (DSPM) is a more recent concept that focuses on securing data across various environments, including cloud, on-premises, and hybrid models. DSPM solutions aim to protect sensitive data from unauthorized access, leakage, and theft, irrespective of its location. These solutions offer a data-centric approach to security, emphasizing the discovery, classification, and protection of data. Key components of DSPM include:
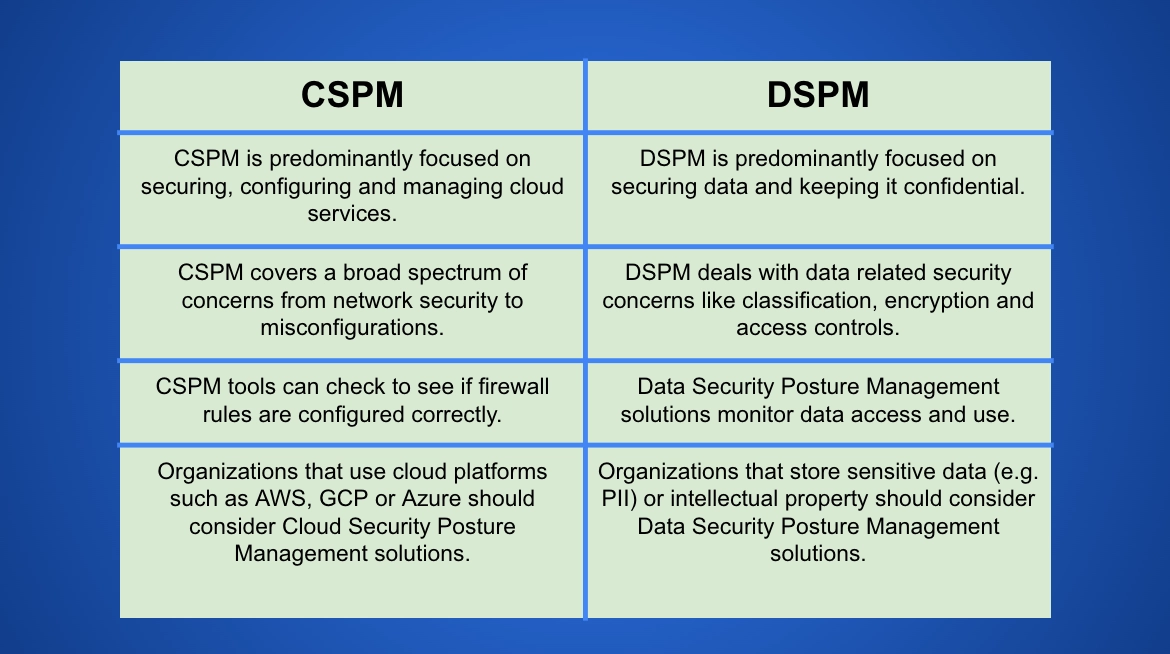 |
Although CSPM and DSPM solutions may overlap in some areas, such as compliance management, they address different aspects of cybersecurity. Here are the key differences:
Focus Area:
Scope:
Objective:
Methodology:
CSPM and DSPM are complementary solutions that, when integrated, provide a holistic approach to cybersecurity. CSPM ensures the cloud environment is secure and compliant, creating a strong foundation for data security. On the other hand, DSPM focuses on protecting the data itself, regardless of where it resides. Together, they enable organizations to achieve a robust security posture that safeguards both their infrastructure and their most critical asset: data.
Neglecting to implement Cloud Security Posture Management (CSPM) or Data Security Posture Management (DSPM) can leave critical vulnerabilities in your defenses, heightening the risk of serious security breaches in your cloud setup or unauthorized exposure of sensitive data.
The absence of CSPM can result in incorrect cloud configurations, creating opportunities for cybercriminals to exploit system weaknesses. Furthermore, it could mean potential threats remain undetected for extended periods, allowing malicious entities to extract a significant amount of your data.
Failing to incorporate DSPM may lead to a heightened likelihood of sensitive data being accessed or disclosed improperly, and a diminished ability to manage and monitor user access to your data resources.
Lacking CSPM or DSPM not only heightens security risks but also increases the danger of failing to meet legal and regulatory standards such as GDPR or HIPAA. This could incur substantial fines and cause lasting damage to your organization's reputation.
As cyber threats evolve and organizations continue to adopt cloud services, the importance of CSPM and DSPM solutions cannot be overstated. By understanding the key differences between these approaches and implementing them effectively, organizations can enhance their security posture, protect sensitive data, and comply with regulatory requirements. While this post provides a comprehensive overview, for those looking to dive deeper into CSPM and DSPM solutions, it's recommended to consult industry-leading sources and platforms like Gartner, Forrester, and the Cloud Security Alliance. These sources offer detailed analyses, best practices, and guidance on selecting and implementing CSPM and DSPM solutions tailored to specific organizational needs.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
