Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Vacations are an opportunity to unwind, explore new places, and escape from the daily grind. With COVID fairly in the rearview mirror, employees are taking off for summer break, many with their company issued laptops in tow. With summer vacation comes access to sensitive data outside of the home office or corporate office, creating the phenomenon of sensitive data going “to the beach” this summer as well.
It’s no surprise that Americans are more likely to bring their laptops on vacations than Europeans. Studies conducted by leading travel technology companies reveal a striking trend among American tourists. According to a 2019 survey approximately 83% of American travelers admitted to carrying their laptops with them on vacations. This high percentage can be attributed to various factors, including the need to stay connected, work remotely, or access personal information during their trips.
With this increased travel comes increased risk:
So how are CISOs to understand the real points of exposure associated with this summer travel?
The questions every company should ask are:
The researchers at Next have investigated activity from hundreds of companies during the period of May to July 2023 to expose that data is in fact “going to the beach," alongside employees this summer.
We looked at two metrics in particular to identify employees not working from their normal location, the number of unique Wi-Fi networks they connect to and the number of unique cities (based on Geo IP location) that agents reported in from.
| Week of May 8 to July 3 2023 comparison |
||
| US | Cities (based on agent IP geo lookup) |
🔼 9.8 % |
| # of unique Wifi connections across all endpoints |
🔼 25.6 % | |
| # of Wifi networks the agent has seen |
🔼 17.9 % | |
| EMEA | Cities (based on agent IP geo lookup) |
🔽 2.9 % |
| Number of Wifi connections across all endpoints |
🔽 9.2 % | |
| Number of Wifi networks the agent has seen |
🔽 13.8 % |
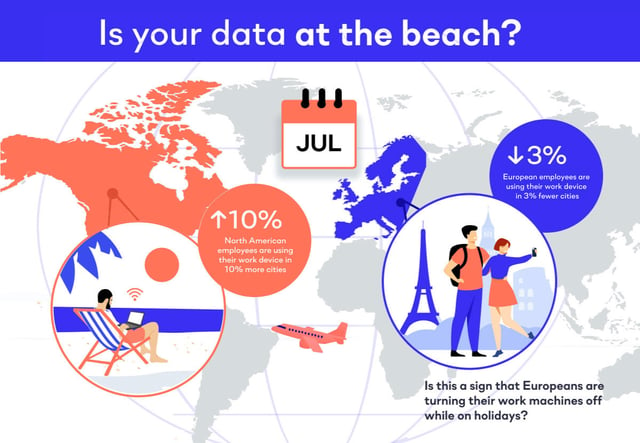
Based on geolocation data, workers in the US are connecting from 10% more cities in July compared to May. In EMEA we see something different, in that workers are connecting from 3% fewer cities during the same time period. 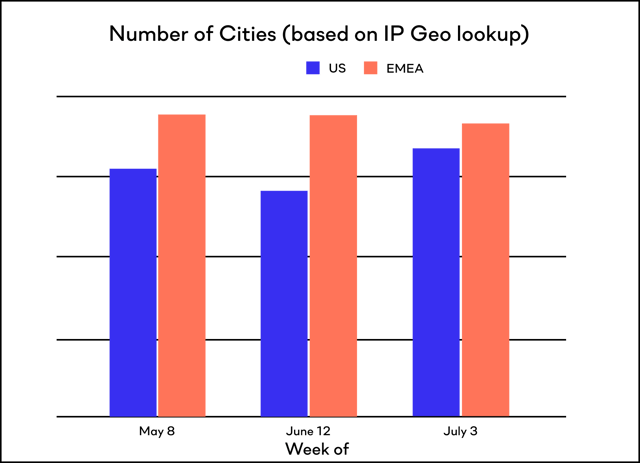
In contrast to their American counterparts, could it be that Europeans display a distinct preference for traveling light when it comes to technology? Or maybe Europeans are better at leaving their work behind, while US employees feel a need to always be available?
Is the data above showing us the differences in work-life balance and vacation culture between the two regions? Americans are known for having longer work hours and fewer vacation days compared to Europeans. This discrepancy often leads to a higher demand for remote work options during trips, prompting many American travelers to carry their laptops.
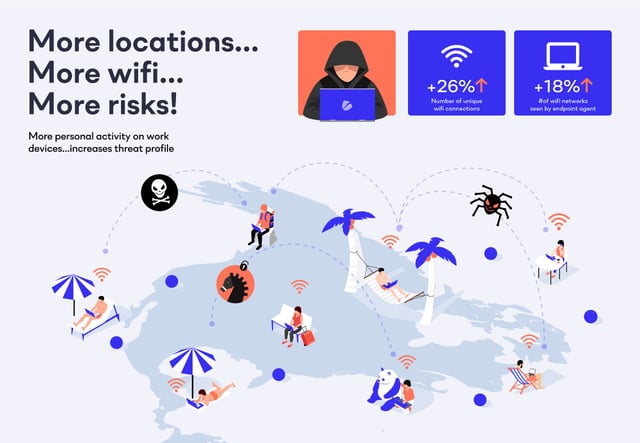
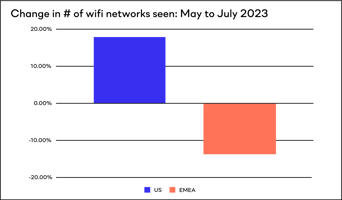 US workers are bringing their work laptop on the road. This means that company data and intellectual property is also on the road, both the data that’s on the laptop but also the data that a worker is accessing from their endpoint. When we look at the number of wifi networks the Reveal agent has seen in a given time period, US Reveal agents see 18% more networks. Whereas EMEA agents see 14% fewer networks for the same period.
US workers are bringing their work laptop on the road. This means that company data and intellectual property is also on the road, both the data that’s on the laptop but also the data that a worker is accessing from their endpoint. When we look at the number of wifi networks the Reveal agent has seen in a given time period, US Reveal agents see 18% more networks. Whereas EMEA agents see 14% fewer networks for the same period.
Now that we are aware of the increased risk that comes with increased travel, what are some of the controls security teams should put in place to protect sensitive data, maintain the integrity of company systems and prevent cyberattacks?
Secure Network and Connectivity: Ensure that home (and vacation) Wifi networks are password protected and use WPA3 encryption and discourage connecting work devices to public Wifi networks. This reduces the risk of attackers on the same network intercepting traffic or exploiting vulnerable software on the device.
Data Encryption: Enforce full drive encryption on company devices and ensure strong passwords are being used. This helps protect sensitive information if devices are lost or stolen.
Multi-Factor Authentication: Implement MFA for accessing company systems, applications, and email accounts. This adds an extra layer of security; something you know + something you have.
Secure file sharing: Implement secure file sharing solutions that allow controlled access to shared files and prevent unauthorized sharing. Users forwarding a sensitive file to their personal device so they can read it by the pool moves it outside of company protection protocols.
Be Prepared: Develop a clear incident response plan that remote workers can follow in case of a security breach or cyber incident.
Demonstrating a robust approach to Information Security risk is not only paramount to maintaining compliance with current and new regulations, like the SEC Cyber Rules but also serves to ensure vital business data is available at the right times but not lost or exfiltrated. By understanding how data is being accessed businesses can make better decisions around preventing it being accessed at the wrong times or avoid simply not knowing from where or how data is being accessed.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
