Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

As corporate workers increasingly rely on Software-as-a-Service (SaaS) applications, including GenAI tools such as ChatGPT, there is a pressing need to gain comprehensive insights into their use to proactively manage and mitigate data exposure risks. Using unauthorized SaaS apps, or Shadow SaaS, puts data at greater risk because your security teams are unaware which applications are being used, no less what data is going into them.
While using Shadow SaaS can seem benign, it carries hidden risks that can undermine an organization's security, compliance, and data integrity. Using real-world data from hundreds of companies using the Reveal Platform by Next DLP in January 2024, this post aims to shed light on these often misunderstood risks, providing insights into Shadow SaaS usage and how Shadow SaaS is being used to exfiltrate company owned data, either inadvertently or maliciously. As part of this study, we first analyzed the top exfiltration Tactics, Techniques and Procedures across the platform, aligned with the MITRE ATT&CK framework and summarized our findings in an earlier blog post.
In this blog post, we focus specifically on file uploads through web-based SaaS applications.
It is up to the organization alone to discern if an app used by an employee is sanctioned or not. Shadow SaaS is considered as such if the application is not sanctioned for use by the IT team. So Google Workspace, for example, could be Shadow SaaS for one organization and a sanctioned coworking platform for another.
Cross referencing the sites that users uploaded data to with some of the most popular knowledge worker apps, we saw many of the business applications you’d expect:
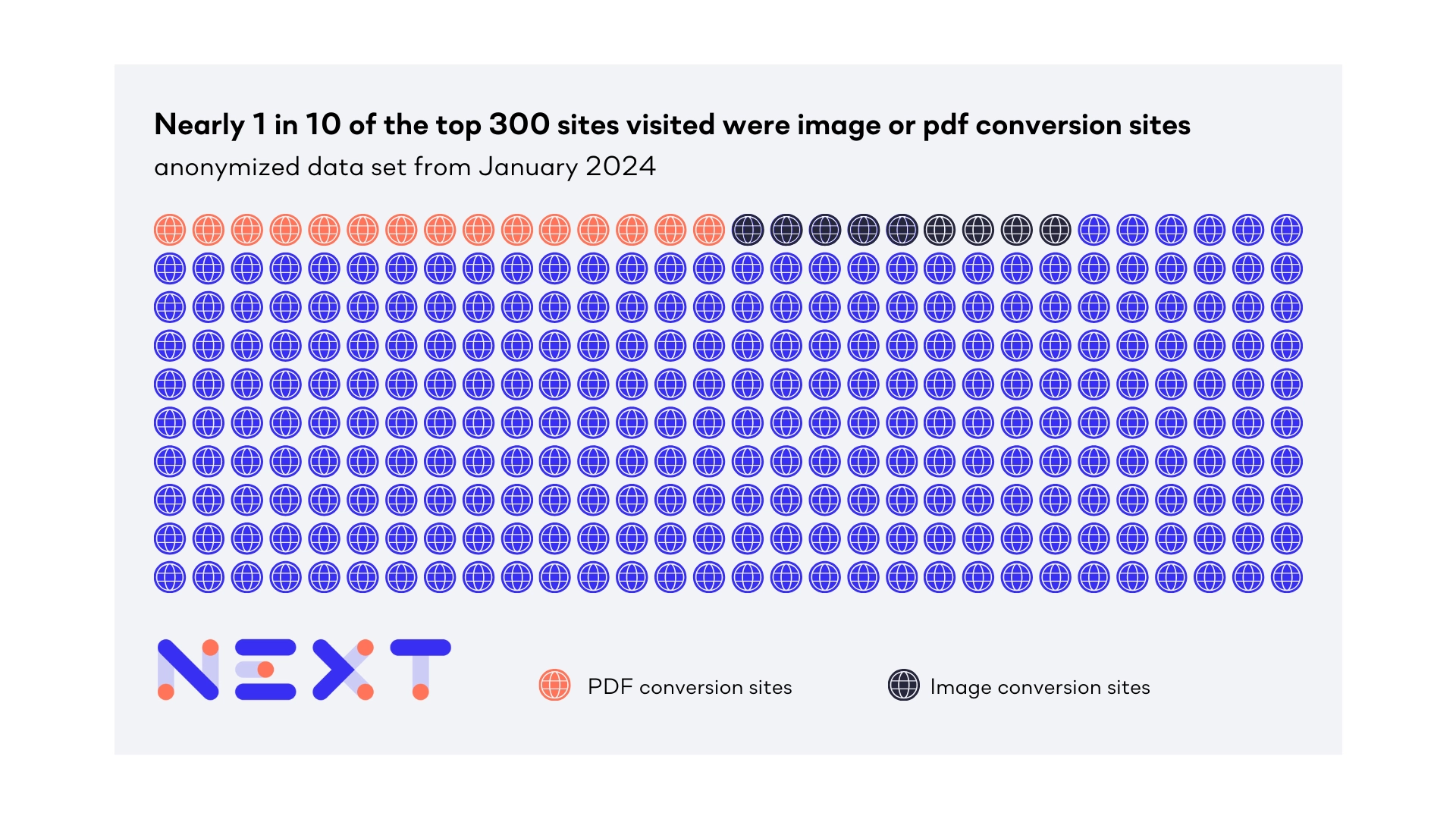
While using a company managed endpoint, there may also be a risk of users uploading data to popular sites and apps that may not pertain to their primary day job, such as:
 |
In addition, we saw:
Across all the sites and applications that users uploaded data to, WhatsApp had the 4th most uploads. This is surprising in that WhatApp isn’t well known as a business application in the geographies where most of Reveal’s users work: US and UK. But at the same time it’s not surprising given how easy the WhatsApp application makes it to copy, paste, and share. All that’s needed is a recipient phone number to transfer data.
WhatsApp isn’t the only messaging app that is being used to share data from managed devices; Facebook had the 28th most uploads and Telegram, an app known to be used by criminals, whistle-blowers, terrorists and hackers, was the 107th most uploaded-to site.
As part of the investigation, we were interested to see how GenAI and ChatGPT usage has changed since our last report.
| March 2023 | August 2023 | January 2024 | |
|---|---|---|---|
| % of companies with at least 1 ChatGPT user | 50% | 97% | 99% |
| % of companies with at least 1 Bard user | 0% | 1% | 5% |
While not GenAI, we also see access to and uploads to services like Stack Overflow. These are messaging boards where tech people ask questions of the community and get advice on coding / config etc. It’s a similar use case as GPT in a lot of ways and has the same risks of employees posting proprietary code or disclosing technical information that is sensitive.
iCloud, given its seamless integration with the wide array of Apple devices prevalent in both personal and professional spaces, presents a potential malicious or negligent vector for data exfiltration from companies. Our researchers noted that iCloud is the 15th most downloaded-from site and the 33rd most uploaded-to.
The ubiquity of Apple products across various levels of an organization's hierarchy allows iCloud to act as an inconspicuous conduit for unauthorized data transfer. Apple's aim to integrate everything and help users have a "cross device" and "data rich experience" could have the effect of putting data into employees’ personal accounts and making it out of reach of organizations governance and control. Employees, intentionally or inadvertently, might sync sensitive corporate data to their personal iCloud accounts, thereby bypassing traditional security measures and making it accessible outside the company's controlled environment.
Looking at where users are downloading files from, we see that sourceforge.com is the 100th most popular site for downloads to company managed endpoints. SourceForge.com and other download sites like it could be a source of shadow IT for several reasons:
Security teams should be asking themselves several critical questions to proactively manage and mitigate the risks associated with Shadow SaaS and potential sensitive data exposure. These include evaluating the extent of unauthorized app usage within their organization, understanding the types of data being transferred to these platforms, and identifying which cloud-based applications are most frequently used for exfiltration purposes. Additionally, they should consider the implications of integrating popular knowledge worker apps with their security protocols and how to better monitor and control data flow to external sites and applications, especially those not directly related to work activities.
Sample questions checklist:
This reflection is essential in crafting a robust security posture that addresses the nuanced challenges of Shadow SaaS in today's digital workplace.
On one hand, Shadow SaaS makes employees more productive by allowing them to use their preferred technologies, which nearly all employees (97%) report increases their productivity. On the other hand, it's well known that Shadow SaaS can pose significant risks by potentially exposing organizations to data breaches, compliance violations, and lack of data governance, as employees use unauthorized software without IT department oversight.
The exploration of Shadow SaaS usage and its role in data exfiltration within organizations highlights a critical vulnerability in modern IT infrastructure. As the adoption of unauthorized cloud-based applications continues to grow, driven by the convenience and ubiquity of services like iCloud and popular knowledge worker apps, the risk of sensitive data being inadvertently or maliciously leaked outside corporate controls also escalates.
We hope this blog post underscores the importance of proactive security measures, robust policy enforcement, and continuous monitoring to mitigate these risks. Through detailed insights and real-world examples, it becomes clear that understanding and addressing Shadow SaaS usage is not just about preventing data loss but also about safeguarding the integrity and reputation of organizations in the digital age.
Shadow SaaS refers to using unapproved Software as a Service (SaaS) applications in an organization without IT’s knowledge. Employees like to use these tools to improve productivity or solve problems, but IT hasn’t sanctioned these applications, which operate outside formal security and compliance protocols. This unauthorized use can create significant security risks, even if employees are trained on cybersecurity best practices.
Shadow SaaS applications create blind spots where IT departments are unaware of all applications in use, leading to gaps in security monitoring. At scale, this increases vulnerabilities, leaks data through unsecured applications, and compromises IT infrastructure integration. Any one of these issues could also cause you to fall out of compliance and put you at risk of regulatory action.
Your business can identify and manage shadow SaaS by:
Enhanced visibility is the best way to prevent shadow SaaS applications from infiltrating your IT infrastructure. Using SaaS management platforms will give you more visibility into all applications, while strict access controls will also limit who can install and use SaaS applications in the first place.
Organizations should also invest in security training, vendor management, incident response platforms, and proper data governance.
Unapproved applications likely don’t comply with industry regulations and standards, opening you up to potential violations. Since you have no control over where and how employees store and use data, you could fall out of compliance with data protection laws. Shadow SaaS also makes it nearly impossible to track and audit this unauthorized use, which further hinders compliance efforts.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
