Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

Trust is an increasingly important topic in businesses. While protecting against insider threats and external hackers remains critical, the “great resignation” and “quiet quitting” have made organizations more aware of the need to build trust relationships with the workforce to improve recruitment, retention, and engagement.
Respecting an individual’s privacy is integral to building trust. It is also an increasingly important regulatory requirement. These regulations, including HIPAA, the California Consumer Privacy Act (CCPA), the Virginia Consumer Data Protection Act, and Europe’s General Data Protection Regulation (GDPR), require organizations to protect the private information of their consumers, customers, and employees.
Employee privacy and data protection are intrinsically linked. Companies implement data protection platforms to be compliant with data privacy regulations, and to ensure access to IP is tightly monitored and controlled. However, privacy concerns arise when workforce surveillance and productivity monitoring is the primary business objective. Research shows that monitoring employee productivity can lower employee morale and job satisfaction. It also reportedly increases stress and the development of stress-related illnesses. There is also evidence that increased monitoring makes employees more likely to break rules.
The risk of employee surveillance abuse also applies to traditional DLP tools where appropriate checks and balances are not in place to prevent privileged admins from abusing access to highly sensitive employee activity data sets. If any IT employee can easily view another employee’s activity, it could include holiday plans, health information, banking details, or event location data. This can lead to bias or abuse. While investigations require watching for suspicious activity, who is watching the watchers?
While all organizations want to trust their employees, the truth is that insider threats are real. As noted, legacy DLP and insider risk solutions allow IT personnel to easily view the activity of individual users. This unfettered access to user activity can lead to bias or abuse.
Reveal takes a different approach. When suspicious activity warrants a deeper probe, investigators can request a “scoped investigation” of a user. Scoped investigations can also be assigned to investigators. A scoped investigation limits what an authorized investigator is allowed to see and the time of the investigation.
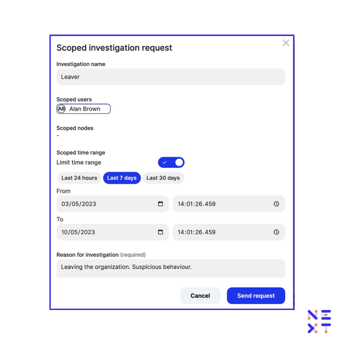
In a scoped investigation, the investigator makes a request or is assigned to view the activity of:
If approved, authorized investigators are granted time-bound, revocable, and audited access to users’ full activity data. In other words, scoped investigations strike a balance between data privacy and information security regulations.
At Next we work hard to help our customers find the balance where security teams have the information they need to protect the organization's data but also where users don;’t feel their privacy is put at risk. Paired with other Reveal data minimization techniques, such as pseudonymization, scoped investigations allow security analysts to detect and mitigate threats while maintaining data privacy and the confidentiality of users.
These build employee trust while protecting IP, trade secrets, employee information, and other sensitive data. Scoped investigations end the practice of unfettered monitoring of individuals, while pseudonymization protects user identity. You can learn more by contacting our team today.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
