Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
The US government has long been concerned with cybersecurity. This is particularly true for critical infrastructure, including energy production, telecommunications, banking, healthcare, food and agriculture, emergency services, and other industries. In 2013, President Obama issued Executive Order 13636 calling for “Improving Critical Infrastructure Cybersecurity.” The Order included a requirement to develop a Cybersecurity Framework that organizations could leverage to manage cybersecurity risk.
The National Institute of Standards and Technology (NIST) was entrusted with creating the framework. In February 2014, NIST introduced version 1.0 of the Cybersecurity Framework (NIST CSF). The NIST CSF has three primary components.
The Framework Core describes activities, outcomes, and references about aspects and approaches to cybersecurity. In NIST CSF v1, it was composed of five “Functions,” with each Function having one or more Categories of activities that organizations can adopt to reduce risk. The five functions of CSF 1.0 and 1.1 are:
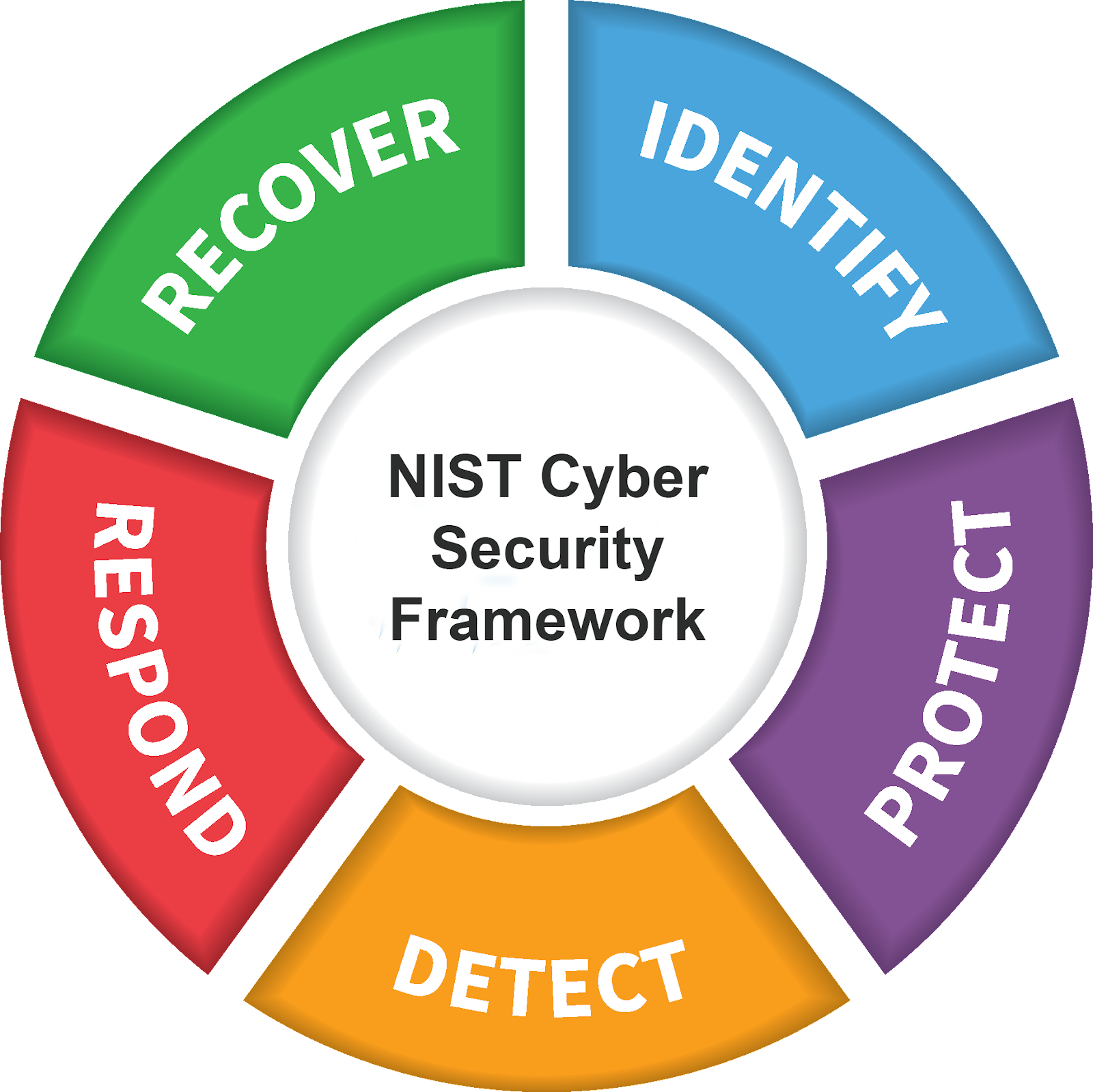
|
The Framework Implementation Tiers provide a structure for gauging and communicating organizations' cybersecurity risk management approaches. Tiers range from “Partial” (Tier 1) where risk management is ad hoc, to “Adaptive” (Tier 4) where organizations have a dynamic and evolving approach to cybersecurity risk management.
The Framework Profile is a list of security activities and desired outcomes an organization has selected based on their specific cybersecurity goals, risk tolerance, regulatory requirements, and business objectives.
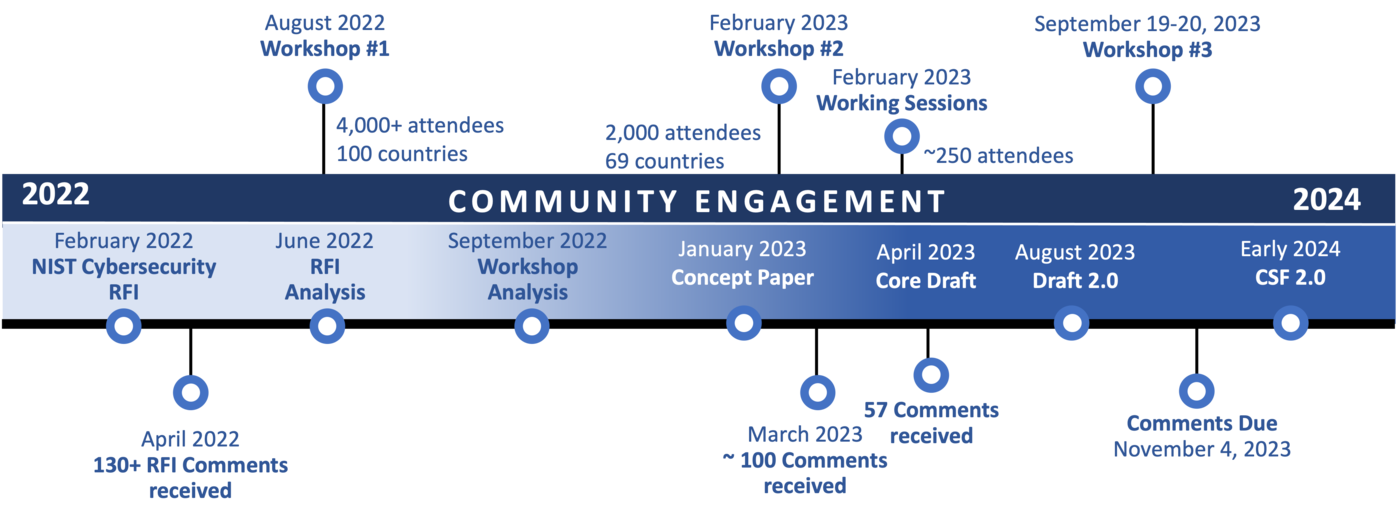
As the threat landscape evolves, so too should security countermeasures. NIST issued an update to the CSF in 2018. In early 2022, NIST decided to revisit the CSF again. Their early goal was to encourage adoption of the CSF across organizations beyond the critical infrastructure industries, including small businesses and schools. After a Request for Information, hundreds of comments from industry participants, and a series of workshops to receive feedback, NIST released the CSF 2.0 draft on August 8, 2023. Comments on the draft are due November 4 and a final release of CSF 2.0 is expected in early 2024.
|
The new draft includes several major changes based on the security landscape and stakeholder feedback. These include:
Recognition of its broad use: The CSF was created in response to threats to the nation’s critical infrastructure. Recognizing the adoption of the CSF across organizations of all sizes and industries, the official name of the CSF has been changed from “Framework for Improving Critical Infrastructure Cybersecurity” to simply “Cybersecurity Framework.”
Increase guidance on CSF implementation: NIST has updated and expanded the Framework Profiles guidance and added implementation examples. Also included are templates organizations can use or adapt to their needs to assist with rolling out the framework.
An emphasis on supply chain security: Before the Target breach in 2013, many organizations assumed supply chain security was not their responsibility. Today more organizations recognize that their vendors and partners can represent a weak link in their defenses. The updated CSF adds “Cybersecurity Supply Chain Risk Management as a Category in the new Governance Function. It includes defining processes for identifying, managing, and monitoring supply chain risk.
Relate CSF to other Frameworks and resources: Navigating the various standards can be confusing. CSF 2.0 includes new references to NIST Privacy Framework, NICE Workforce Framework for Cybersecurity (SP 800-181), Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (SP 800-161r1), and others.
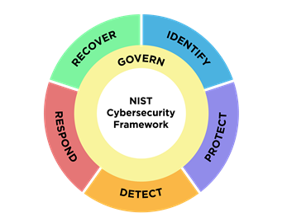
Addition of security governance: NIST has added a sixth Function to the Framework Core: Govern. The Govern Function is designed to “Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy.” In addition to the Supply Chain Risk Management Category discussed above, it includes activities for:
|
Because of the broad adoption of the CSF beyond the critical infrastructure industries, we expect organizations to continue to view CSF as a robust template for improving their cybersecurity. In particular, the emphasis on supply chain security will trickle down to midsize businesses. Midsize businesses often rely on an extensive supply chain network to compete with more prominent players, magnifying the risk of a supply chain breach.
Security teams should also remember that these changes do not reduce the Frameworks focus on data security. The Govern Function is additive. Teams must continue to focus on the other functions of identifying security risks, detecting attacks and compromises, responding to incidents, and recovering from cybersecurity attacks.
Are you curious how Reveal can help with the six functions in the proposed v2,0 framework? Book a demo and see how our out-of-the-box policies support compliance efforts on day one. Our policy-free deployment helps you discover risks you weren’t even aware of for future-proofed Data Loss Prevention and Insider Risk Management.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources

