Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release
|
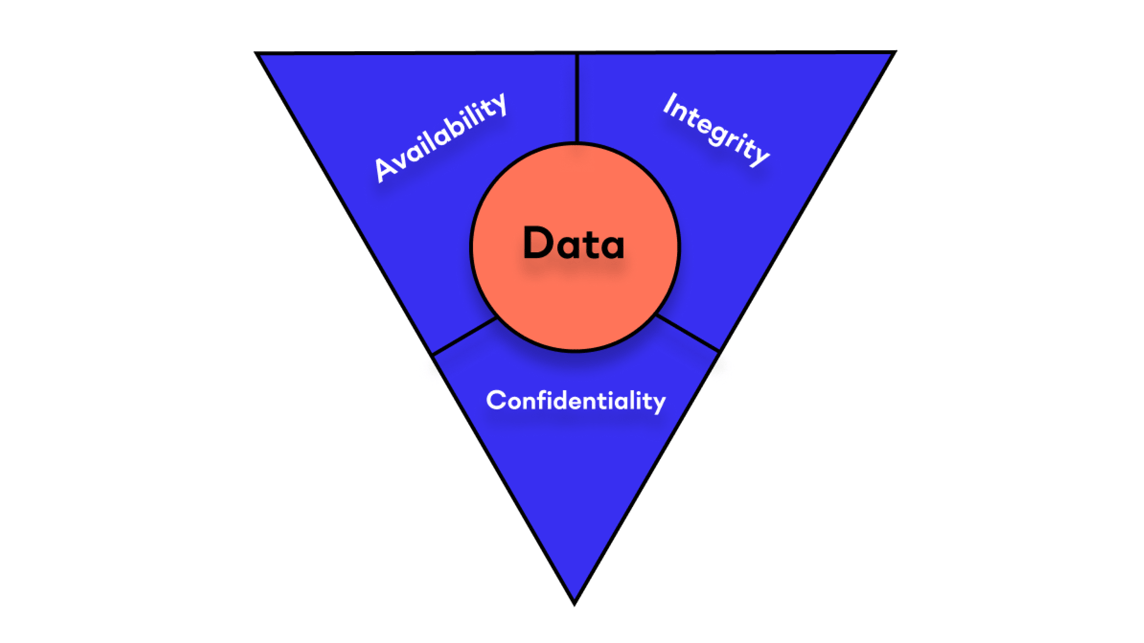
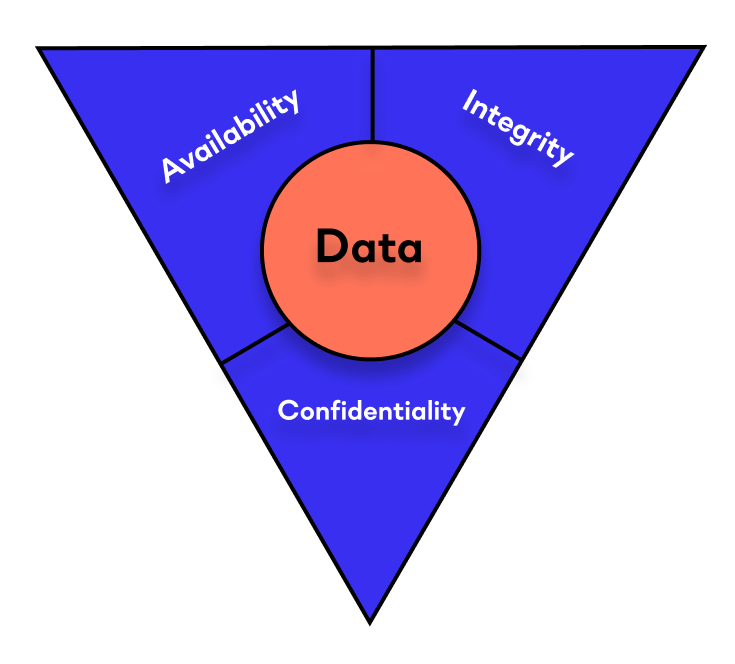
The CIA triad, or the Information Security Triad, serves as a framework to guide cybersecurity efforts and helps organizations identify potential vulnerabilities and risks. Let's delve deeper into each element of the CIA triad and understand their significance in fortifying cybersecurity:
Confidentiality:
Confidentiality pertains to the protection of sensitive data from unauthorized access and disclosure. It ensures that information is accessible only to those with the appropriate privileges, preventing unauthorized individuals or entities from viewing, using, or modifying sensitive data. Encryption, secure access controls, and authentication mechanisms are vital tools that help maintain confidentiality.
For businesses, safeguarding customer data and proprietary information is crucial to maintaining trust and credibility. In some cases, it's also required for compliance with lawful regulations in a given industry. Businesses that fail to meet compliance requirements face fines and other penalties. For governments, ensuring the confidentiality of classified information is essential for national security and diplomatic relations.
Integrity:
Integrity focuses on maintaining the accuracy and trustworthiness of data and ensuring that it remains unaltered and reliable. Data integrity measures protect against unauthorized modification, deletion, or corruption of information, preserving its accuracy and authenticity. Techniques like hashing, digital signatures, and version control help maintain data integrity.
Data integrity is critical for both individuals and organizations. In a digital landscape where data manipulation and misinformation are prevalent, ensuring the integrity of financial records, legal documents, and critical communications is vital for making informed decisions and establishing credibility.
Availability:
Availability guarantees that information and services are accessible to authorized users when needed. Cybersecurity efforts must ensure that systems and data are resilient against downtime, denial-of-service attacks, or other disruptions. Redundancy, fault-tolerant systems, and disaster recovery plans are strategies to ensure availability. Because business increasingly relies on online platforms and services, ensuring continuous availability is paramount to prevent financial losses and maintain customer satisfaction. For essential services like healthcare and emergency response systems, availability can be a matter of life and death.
While the CIA triad has been a cornerstone of cybersecurity practices, modern challenges have pushed for its evolution and expansion. As technology advances, cybersecurity has expanded beyond traditional systems, including cloud computing, the Internet of Things (IoT), and artificial intelligence. The CIA triad, therefore, needs to be supplemented with other principles such as accountability, auditability, and non-repudiation to address contemporary threats comprehensively.
Moreover, human factors play a significant role in cybersecurity, as many breaches result from social engineering and insider threats. Organizations must invest in employee training and awareness programs to promote a security-conscious culture.
The CIA triad remains a fundamental framework for guiding cybersecurity practices. It emphasizes the core pillars of confidentiality, integrity, and availability, which are crucial for securing sensitive data and protecting critical systems. However, cybersecurity is a dynamic field; continuous adaptation and enhancement of security measures are necessary to stay ahead of evolving threats. By integrating the principles of the CIA triad with cutting-edge technologies and a human-centric approach, organizations can build resilient and robust cybersecurity defenses to thrive in the digital era.
Get a demo of the Reveal platform from Next. We’ll show you how our unified data loss prevention and insider risk management platform can improve your data's confidentiality, integrity, and security.
The CIA triad is a cybersecurity model that stands for Confidentiality, Integrity, and Availability. It guides organizations in securing their sensitive information and systems by focusing on these three critical principles.
Yes, although it’s just one part of an organization’s overall security culture. Organizations must also address security concerns in cloud computing, Internet of Things (IoT) devices, and artificial intelligence (AI). Plus, human factors like social engineering and insider threats also require employee training and awareness programs.
Accountability ensures that actions can be traced back to responsible individuals, auditability allows for the tracking and review of activities, and non-repudiation prevents individuals from denying their actions. These principles work well with the CIA triad, helping organizations comprehensively address contemporary threats.
Any organization that processes data can benefit from following the principles of the CIA triad, including:
A DLP platform supports confidentiality, integrity, and availability at scale to protect an organization’s sensitive data. It does so in multiple ways, including:

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources