Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

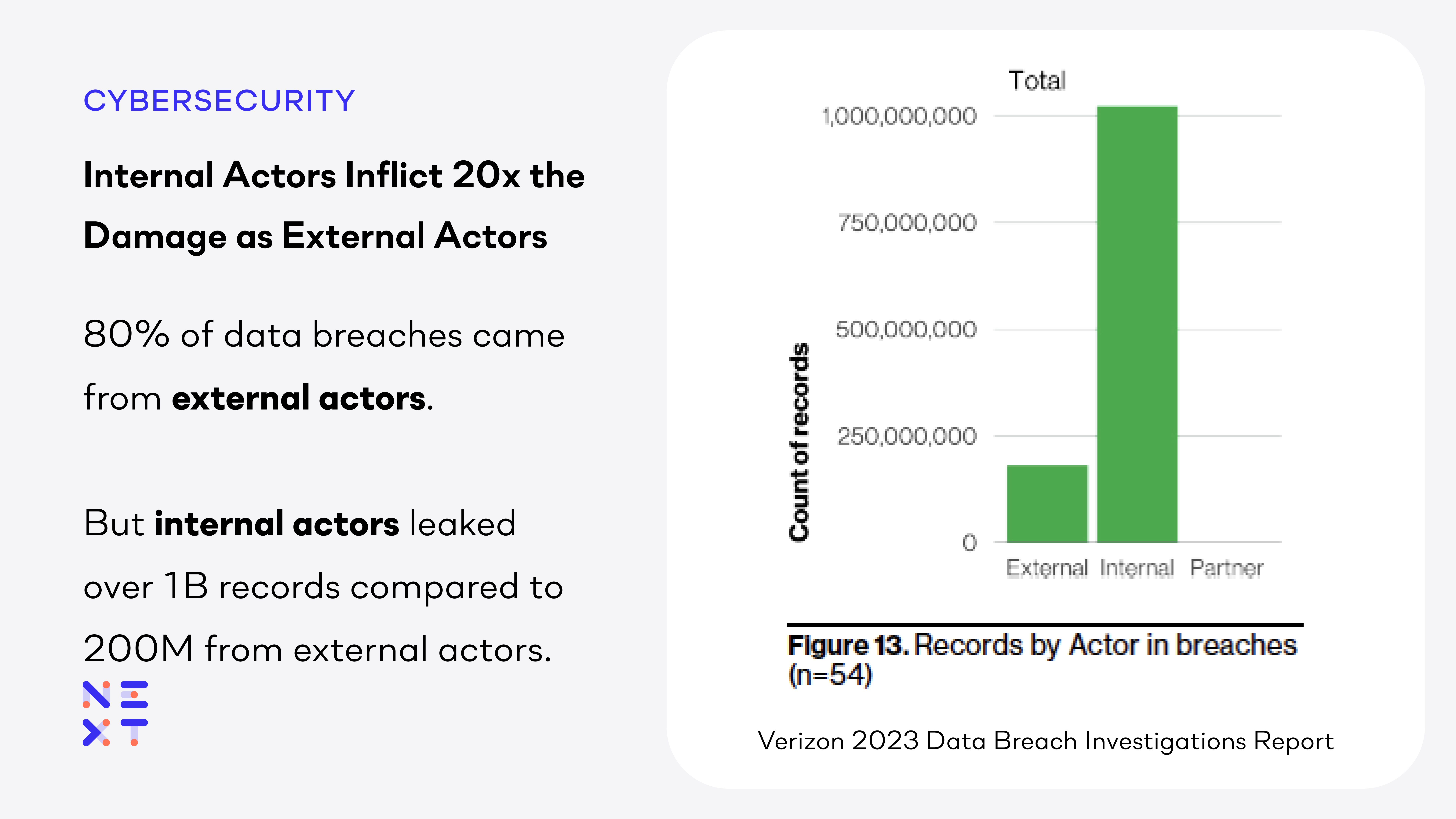
While many organizations are reluctant to admit it, insider threats present significant risks to intellectual property, trade secrets, and regulated data such as personally identifiable information (PII) and personal health information (PHI). How much risk? According to the Verizon Data Breach Investigation Report (DBIR), while insiders were responsible for 20% of all data breaches, they inflicted 20x the damage. Despite fewer incidents, internal actors leaked ~1 billion records vs. 200 million records from external actors. Further into the report, 39% of the breaches in the healthcare segment and 24% of breaches in small businesses were by insiders. Another study found that more than two-thirds (68%) of data breaches at UK law firms are caused by insiders.
 |
Insider attacks are not restricted to the private sector, of course. Malicious insiders – spies – have stolen government secrets for as long as there have been governments. More recently, we have seen a Massachusetts Air National Guardsman charged with leaking highly classified military documents.
Chelsea Manning, a former intelligence analyst for the U.S. Army, leaked hundreds of thousands of classified documents to WikiLeaks in 2010, including sensitive diplomatic cables and military reports. This breach of classified information compromised national security and strained diplomatic relations. It emphasized the importance of insider threat programs in identifying individuals who may pose a risk to sensitive data and implementing measures to prevent unauthorized disclosures.
In 2011, a year after the Wikileaks breach, President Obama issued Executive Order (E.O.) 13587, directing federal agencies with access to classified information to establish insider threat detection and prevention programs. The EO included an order to develop the National Insider Threat Task Force (NITTF). In September 2019, the first National Insider Threat Awareness Month was launched. It aims to bring together security and privacy resources from the government and industry to build awareness of the risks posed by insider threats and the benefits of insider threat programs.
We have previously written that not all insiders are threats, but anyone with access to sensitive data presents a risk. This can include employees, partners, vendors, and others with legitimate access to organizational resources. Outsiders posing as insiders present a separate but related challenge. After all, an outsider with stolen credentials appears benign until they show their intentions.
Insider threats are not limited to large organizations or government agencies. Small and medium-sized enterprises (SMEs) are equally vulnerable. In 2014, a former healthcare company employee in the United States was found guilty of stealing patient data and selling it to identity thieves. This incident not only compromised the privacy and security of patients but also resulted in significant financial losses for the company. It emphasized the need for SMEs to implement insider threat programs tailored to their specific needs and resources.
Starting an insider threat program doesn’t need to be daunting. The ability to detect, hold, and block attacks is a prominent component. Doing so when the attacker is authorized to access sensitive data is difficult. We break this down into a few requirements:
Classify sensitive data as it is created and used:
Legacy insider threat and data loss prevention solutions require teams to identify and classify all sensitive data before data protection can begin. This leaves organizations vulnerable during the process – plenty of time for a malicious insider to cause harm. Instead, Reveal classifies all data as it is accessed or created by users.
Understand intent:
Legacy solutions rely on static rules dictating what actions each class of users can take with each data class. The inevitable false positives frustrate users and security teams; false negatives might be even worse. Reveal moves machine learning to each endpoint to solve this problem. It quickly builds a baseline for each user and endpoint to identify anomalies and discern intent based on the users, data, and actions. Our “policy-free” approach reports on risks to data without preset rules.
Containment:
Attacks are unavoidable. When an attack is identified, the team aims to contain it immediately. With Reveal, customers can isolate devices from the network to prevent the incident from spreading further, lock out user sessions, take screenshots to gather evidence, display messages, block uploads, and kill processes to protect their organization.
National Insider Threat Awareness Month includes three other “best practices” that we believe are important:
Insider threat programs are designed to detect and block malicious or careless insiders from exposing sensitive data. National Insider Threat Awareness Month also makes it clear in the FAQ that it is critical to respect the “privacy and civil liberties” of insiders in addition to managing risk.
Unlike legacy DLP solutions, we took a privacy-by-design approach to Reveal. It uses pseudonymization while detecting and mitigating threats without compromising users' privacy and preventing bias in monitoring users’ activities. Scoped investigations limit what an investigator is allowed to see and the time of the investigation.
Insider Threat Awareness Month is a good thing. It brings needed attention to a problem the industry continues to address. An effective insider threat awareness program cannot ignore accidental data loss and must be practiced 12 months of the year. Ongoing, incident-based training is critical to building a security-positive culture and mitigating the risk of unintentional data leakage.
Read more about Reveal’s insider risk management solution. Ready to see how it can help your team identify insider risks before they become a data breach? Contact us for a customized demo.
National Insider Threat Awareness Month (NITAM) is an annual event held in September. It’s dedicated to raising awareness about the risks posed by insider threats and encouraging businesses to follow best practices to mitigate these risks.
Government agencies and cybersecurity professionals promote ITAM to educate and inform organizations, and especially their employees, about the importance of detecting and reporting insider threats.
ITAM raises awareness of the potential dangers of insider threats, which many employees might not take seriously. This event encourages organizations to be more vigilant and proactive in taking action against insider threats, giving them the opportunity to strengthen their security posture.
The ultimate hope is that NITAM will cultivate a positive culture of cybersecurity awareness and responsibility, preserving consumer trust and enhancing security for all.
Organizations can join Insider Threat Awareness Month by:
Insider Threat Awareness Month is multi-faceted, with goals to:

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
